Process Memory View is a cool little memory tool! Do not press backspace in the Hex View, it will delete a byte so when you poke it messes it all up.. idrc to fix it. If anyone wants it, I can make a much much better tool later.
Edit the ip file and change it to your PlayStation's ip address, make sure you have jkpatch loaded first. If your console goes into rest mode, then doing anything with RPC may crash it.
Download: memview-r4.zip (45.57 KB)
Look at the release page for payload.bin and kpayload.bin!
Use the send.sh bash script to easily send it to the console!
To be honest, this is not about the Memory View tool... This is about jkpatch! A little project I have been working on. I want the community to help me develop this, so please send some pull requests or open an issue!
The RPC networking is light speed! On LAN there is basically no latency.
Please help commit to my project!
https://github.com/xemio/jkpatch
And from the README.md: Jailbreak Kernel Patches
Spoiler
 Update: Here is a new version with a reboot function, peek/poke unlimited length, and save view bytes to file. Also the hex view will now prevent you from inserting/deleting bytes. Oh also the memory map view looks 100x better, and you can see all the mappings now.
Update: Here is a new version with a reboot function, peek/poke unlimited length, and save view bytes to file. Also the hex view will now prevent you from inserting/deleting bytes. Oh also the memory map view looks 100x better, and you can see all the mappings now.
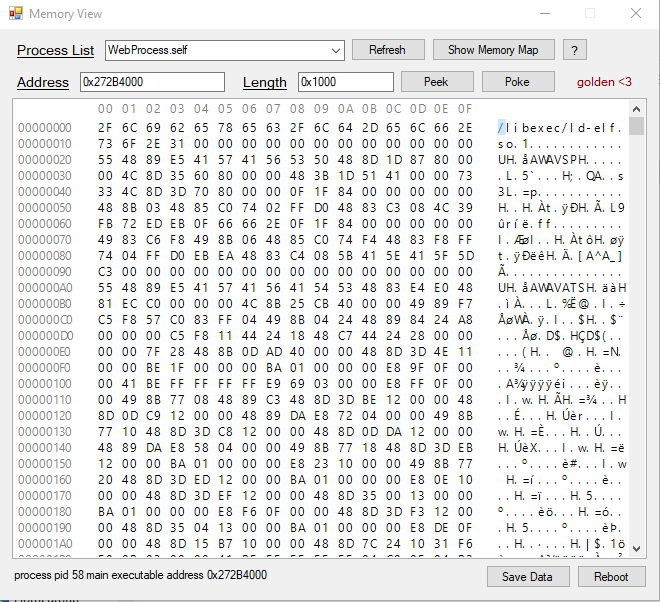
I have also build the latest version of librpc and jkpatch for you all:
https://github.com/xemio/jkpatch/releases/tag/1
golden
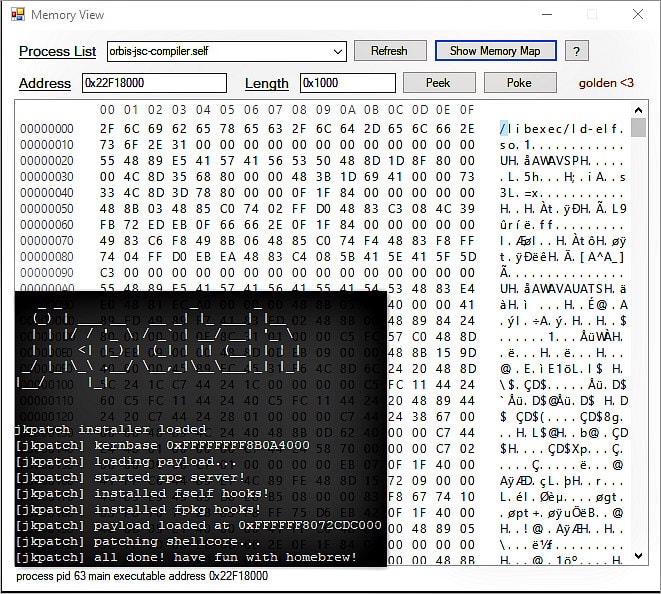
Edit the ip file and change it to your PlayStation's ip address, make sure you have jkpatch loaded first. If your console goes into rest mode, then doing anything with RPC may crash it.
Download: memview-r4.zip (45.57 KB)
Look at the release page for payload.bin and kpayload.bin!
Use the send.sh bash script to easily send it to the console!
To be honest, this is not about the Memory View tool... This is about jkpatch! A little project I have been working on. I want the community to help me develop this, so please send some pull requests or open an issue!
The RPC networking is light speed! On LAN there is basically no latency.
Please help commit to my project!
https://github.com/xemio/jkpatch
And from the README.md: Jailbreak Kernel Patches
Spoiler
I have also build the latest version of librpc and jkpatch for you all:
https://github.com/xemio/jkpatch/releases/tag/1
golden

