Following Parts 1 through 3 of their PS4 Aux Hax covering hacking Aeolia, Syscon and DS4 today PlayStation 4 hackers fail0verflow shared documentation on PS4 Aux Hax 4 which uses HDMI (High-Definition Multimedia Interface) CEC (Consumer Electronics Control) to get code exec on all PS4 Belize southbridge versions (including PS4 Pro, etc) without requiring other parts of the system to be pwned! 
According to Wikipedia, CEC is a feature of HDMI designed to allow users to command and control devices connected through HDMI by using only one remote control... and the bug is in the HDMI CEC code with the path reachable when HDMI-CEC is enabled and active.
Be sure to check out the full PS4 Aux Hax 4: Belize via CEC documentation on their latest Blog Entry alongside the PS4 Southbridge Reverse-Engineered Code Examination, and to quote in part:
"So, the overall process is like:

This post outlines a way to dump EMC firmware and gain EMC code exec on any hardware revision. While the real root keys (in fuses and ROM) of EMC versions besides the first are still unknown, they could yet be recovered with side channel attacks, if someone really wanted them. Since this method is comparatively much more simple and more generic, it stands on its own as an interesting exploit.
As was hinted at, the CXD90046GG version of EMC employs slightly better security practices. The EMC ROM now wipes the SRAM space used as stack during initial key derivation, and some as-of-yet unknown method is used to unmap the ROM, mitigating it being dumped simply by reading from address 0x00000000. Again, it is likely the key material could still be recovered - if someone cares - but it’s interesting to see that such changes made their way into hardware between revisions."
Spoiler: Related Tweets
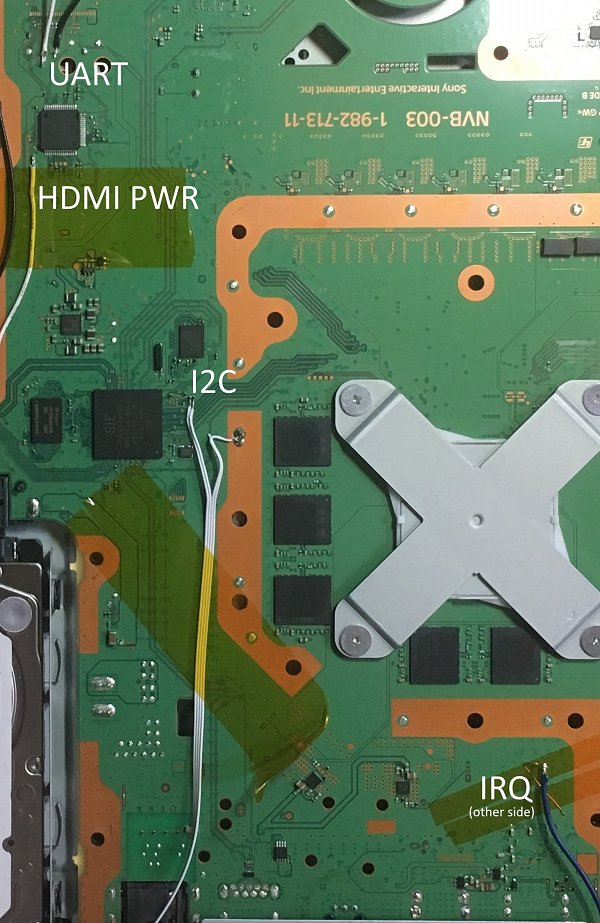
According to Wikipedia, CEC is a feature of HDMI designed to allow users to command and control devices connected through HDMI by using only one remote control... and the bug is in the HDMI CEC code with the path reachable when HDMI-CEC is enabled and active.
Be sure to check out the full PS4 Aux Hax 4: Belize via CEC documentation on their latest Blog Entry alongside the PS4 Southbridge Reverse-Engineered Code Examination, and to quote in part:
"So, the overall process is like:
- Tap onto CEC-related i2c and irq lines and HDMI encoder power switch
- Power up PS4 and enter Rest Mode
- Wait for “EAP running” message from custom EAP kernel
- Induce the CEC RX interrupt
- Feed data to EMC such that it causes a stack buffer overflow
- Wait for EMC to copy SRAM to DDR3
- Dump copied SRAM out of UART
This post outlines a way to dump EMC firmware and gain EMC code exec on any hardware revision. While the real root keys (in fuses and ROM) of EMC versions besides the first are still unknown, they could yet be recovered with side channel attacks, if someone really wanted them. Since this method is comparatively much more simple and more generic, it stands on its own as an interesting exploit.
As was hinted at, the CXD90046GG version of EMC employs slightly better security practices. The EMC ROM now wipes the SRAM space used as stack during initial key derivation, and some as-of-yet unknown method is used to unmap the ROM, mitigating it being dumped simply by reading from address 0x00000000. Again, it is likely the key material could still be recovered - if someone cares - but it’s interesting to see that such changes made their way into hardware between revisions."
Spoiler: Related Tweets

