It's been awhile since we last heard from Fail0verflow on PS4 Crashdumps and Kernel Dumping, but today they've made available a new trio of PlayStation 4 hacking documentation dubbed PS4 Aux Hax covering hacking the Aeolia (Southbridge), Syscon (System Controller) and DS4 (DualShock 4 Controller) for other developers to learn from! 
The PlayStation 4 research can be found on their blog at Fail0verflow.com in the following pages for those who'd like to read through all the juicy details:
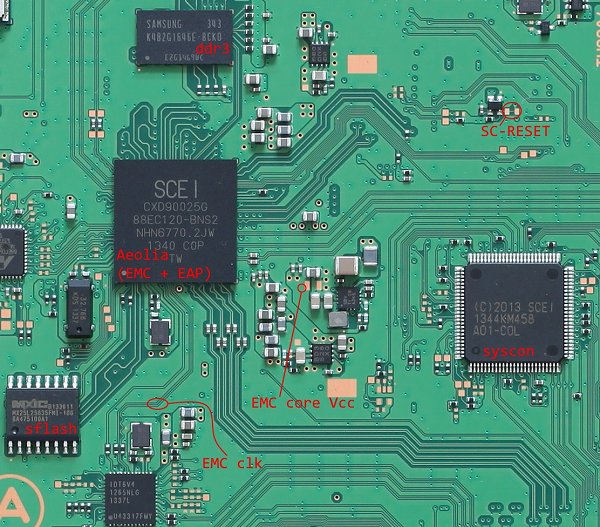
They also credit Volodymyr Pikhur for EAP / EMC work done including side-channel analysis, glitching and ROM recovery in his PS4 IPL AES + HMAC Key Recovery project, the original exploit and Recon Brussels 2018 presentation and PlayStation 4 developer @flatz who aided with reversing, bug hunting and hinted earlier today at signing PS4 CFW (PS4 Custom Firmware) through this research... although @Abkarino of Team Rebug also reminds everyone that more hardware exploiting work is necessary.
PlayStation 4 developer @xxmcvapourxx announced on Discord earlier today the following update synopsis, to quote:
"We could see possible of downgrade of PS4. Dont ask eta. No one ask about if this leads to 5.55 exploits just read."
Similar to the PS3, if a PS4 downgrader is a possibility in the future then less emphasis may be placed on decrypting newer PS4 kernels (such as the 6.00.elf / 6.00.i64 in PS4 Beta Firmware 6.00) in search of exploits and vulnerabilities with more focus on other areas of PlayStation 4 homebrew development.
From Pastebin.com- PS4 SYSCON KEYS:
PS4 FW AES Key SHA 256 Hash: a8e7c33718e3b5a83e0fee1092b1b8cdc851115c94a381816295e22752893ce0
From kiwidog: Slow your roll there, this is just for the ARM chip, just like with the 5.01 EAP hack that was shown before, you will have NOTHING more than that, which is useless for 99.9% of people. Older firmwares didn't even have encryption NOR signing, just compile a elf and replace it and it booted. This has 0 affect on SAMU nor x64 and will not lead to downgrading or a hack (without a replay)
NEEDS KEY FROM SAMU WHICH WONT LEAK. THIS IS ALSO SPECIFICALLY FOR THE ARM CHIP NOT SAMU OR X64.
Also from kiwidog: It is something just not for end users. After discussing with shuffle and getting a bit more clarification. If you were to backup this communication you could replay it with hardware to downgrade, but ONLY TO FIRMWARES WHERE YOU CAPTURED THIS COMMUNICATION. Meaning everyone already on a non-hackable (to roll back to) firmware is out of luck.
Idea being, you were on 1.01, updated and captured when you went to 1.76, then you updated to 5.55, you could use your previously captured communication to downgrade back to 1.76 (allegedly/may be more information needed, but I have 0 reason to doubt shuffle/f0f). For everyone else, it's pretty much useless.
But I could see possibly if a modchip was designed around this principal, you could go online, grab your activation and rifs, downgrade back to a hackable firmware. You wouldn't be able to USE anything on the latest FW that you installed/customized, but when you roll back it should work (if the new games/apps don't require that latest fw).
From Pastebin.com- PS4 Keys:
To quote: Small update to Aux Hax: Nearly same methods are working against devices on recent PS4 Pro board NVB-003: Syscon A05-C0L2 (R5F101LL) Belize southbridge (CXD90046GG) Belize has ROM readout protection and clears stack... they're learning 
The PlayStation 4 research can be found on their blog at Fail0verflow.com in the following pages for those who'd like to read through all the juicy details:
They also credit Volodymyr Pikhur for EAP / EMC work done including side-channel analysis, glitching and ROM recovery in his PS4 IPL AES + HMAC Key Recovery project, the original exploit and Recon Brussels 2018 presentation and PlayStation 4 developer @flatz who aided with reversing, bug hunting and hinted earlier today at signing PS4 CFW (PS4 Custom Firmware) through this research... although @Abkarino of Team Rebug also reminds everyone that more hardware exploiting work is necessary.
PlayStation 4 developer @xxmcvapourxx announced on Discord earlier today the following update synopsis, to quote:
"We could see possible of downgrade of PS4. Dont ask eta. No one ask about if this leads to 5.55 exploits just read."
Similar to the PS3, if a PS4 downgrader is a possibility in the future then less emphasis may be placed on decrypting newer PS4 kernels (such as the 6.00.elf / 6.00.i64 in PS4 Beta Firmware 6.00) in search of exploits and vulnerabilities with more focus on other areas of PlayStation 4 homebrew development.
From Pastebin.com- PS4 SYSCON KEYS:
Code:
FW_AES
5301C28824B57137A819C042FC119E3F
FW_CMAC
8F215691AC7EF6510239DD32CC6A2394
PTCH_AES
EF90B21B31452379068E3041AAD8281E
PTCH_CMAC
95B1AAF20C16D46FC816DF32551DE032
RL78_ID
3A4E6F743A557365643AFrom kiwidog: Slow your roll there, this is just for the ARM chip, just like with the 5.01 EAP hack that was shown before, you will have NOTHING more than that, which is useless for 99.9% of people. Older firmwares didn't even have encryption NOR signing, just compile a elf and replace it and it booted. This has 0 affect on SAMU nor x64 and will not lead to downgrading or a hack (without a replay)
NEEDS KEY FROM SAMU WHICH WONT LEAK. THIS IS ALSO SPECIFICALLY FOR THE ARM CHIP NOT SAMU OR X64.
Also from kiwidog: It is something just not for end users. After discussing with shuffle and getting a bit more clarification. If you were to backup this communication you could replay it with hardware to downgrade, but ONLY TO FIRMWARES WHERE YOU CAPTURED THIS COMMUNICATION. Meaning everyone already on a non-hackable (to roll back to) firmware is out of luck.
Idea being, you were on 1.01, updated and captured when you went to 1.76, then you updated to 5.55, you could use your previously captured communication to downgrade back to 1.76 (allegedly/may be more information needed, but I have 0 reason to doubt shuffle/f0f). For everyone else, it's pretty much useless.
But I could see possibly if a modchip was designed around this principal, you could go online, grab your activation and rifs, downgrade back to a hackable firmware. You wouldn't be able to USE anything on the latest FW that you installed/customized, but when you roll back it should work (if the new games/apps don't require that latest fw).
From Pastebin.com- PS4 Keys:
Code:
Sha512:
20C0A6CEF170E27F050F4F5B269268C36EA5AC75591C957A7241FD1B1BBDF04ECD1C0594CCBA0CB5A6559F279A2FB71A3DF7CB80AC669AD27919228CC344C14F
0E8ED174506F6920907653782DB245B3AD5037235CD2AB0CE9E23DFB3D8B6A676913C63955CAA226820CA2BF0FBD407E101FF5714BB1CAE08BA0CA487B45B6EA
70761E4DD06961EE8662343D517B6C6381AD2C83103C289B0CDE466B13D8F802C41A14090E962F8D524D03D2C9D5FD05911CF78DF9005F8174CC5EE02EDEE04B
88D3C4A2D6878550553D6CE51390B08AC343FA626A55694FD43847CE9C9A69B1E12415C0CBE4BFD4C3F00C61B8F6B10A55388EED9606582C12364C4C2B2925C3
BB884CCD9219DD7DFA7FCDECCADFBFCF2265722DB769DCEA4C23AA032E0B385BE996D4EB237C62AE2C8A1AF1C50126885C47D89D258ED50E0102C443B80F881D
1B9DFC6132900667819F04EC3158EBA094766E4FFA8ECEED8D9046980FCF19CD29C575F6D750A48363DA00BD4D38830AA7686FA0821EE1BC14D71B62451E2EB3
678D7C92365F752E592F4C6851349E3FC52947907E34C11434573C2248DCB7739A6CA7A49A117EF17DB12CA976E57B97319B2F1D0A605C6B55713398301F4871
79E2DACFD89B04D680066E78EAE13BEE76171E54C5B842A123CB88E84602ADFDD709E66AC35FCD8FD8A749A112403DE432E8DFC6B2A1B9C7C6691CC49AB2BDAB
F082BBC7FC008210260ABCEB280733998CA17092A85E696A00D31697D8FB1DD044FB66353EE0164EC3F0ECF0E77F2FDEF0624134620A08CD9F5C5F32E500D7CC
78E748DD48EF5B6AA1A12D978F40CE998C97B71872D2D60C34892415E5E77F8CAE3D44F095763A462D64E865636B77627599CD96D986A8E1022E5030C2627ED7- PS4 SysGlitch Tool and SysCon Glitching Pinout by VVildCard777
- PS4 Syscon (System Controller) Guide (syscon-guide-main.zip) by @BwE of BetterWayElectronics.com.au

