Hello... it appears a brief presentation from Marcan of Fail0verflow will be shown at this year's Chaos Computer Club (CCC) covering Penguins on Aeolia (Embedded Linux) on the PS4 
 Update: PS4 3.55 Full Browser FileSystem and Gadget List
Update: PS4 3.55 Full Browser FileSystem and Gadget List
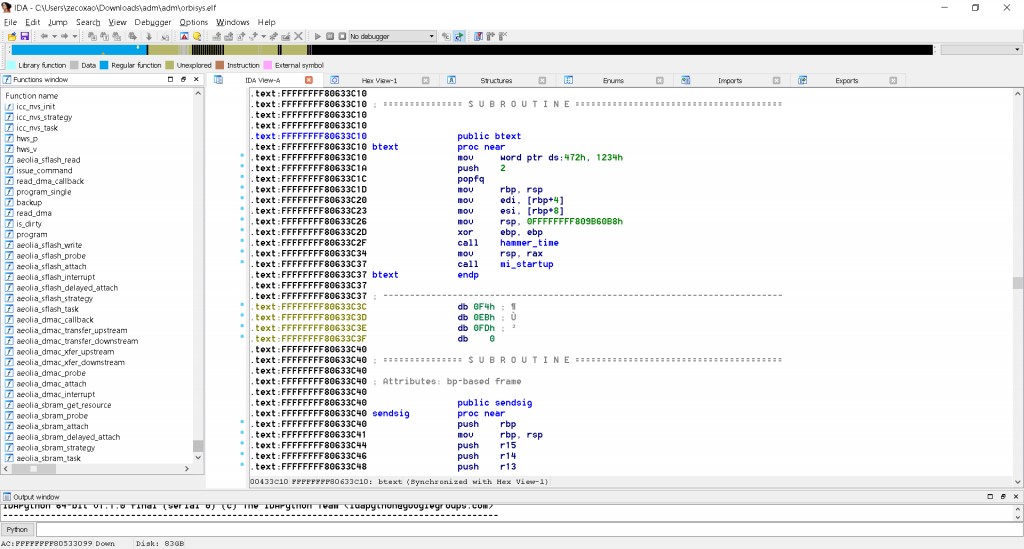
From Wololo: Zecoxao, who's very close to the PS3/PS4 dev scene, shared a screenshot on Twitter, showing some reverse engineering work on what appears to be PS4 system files:
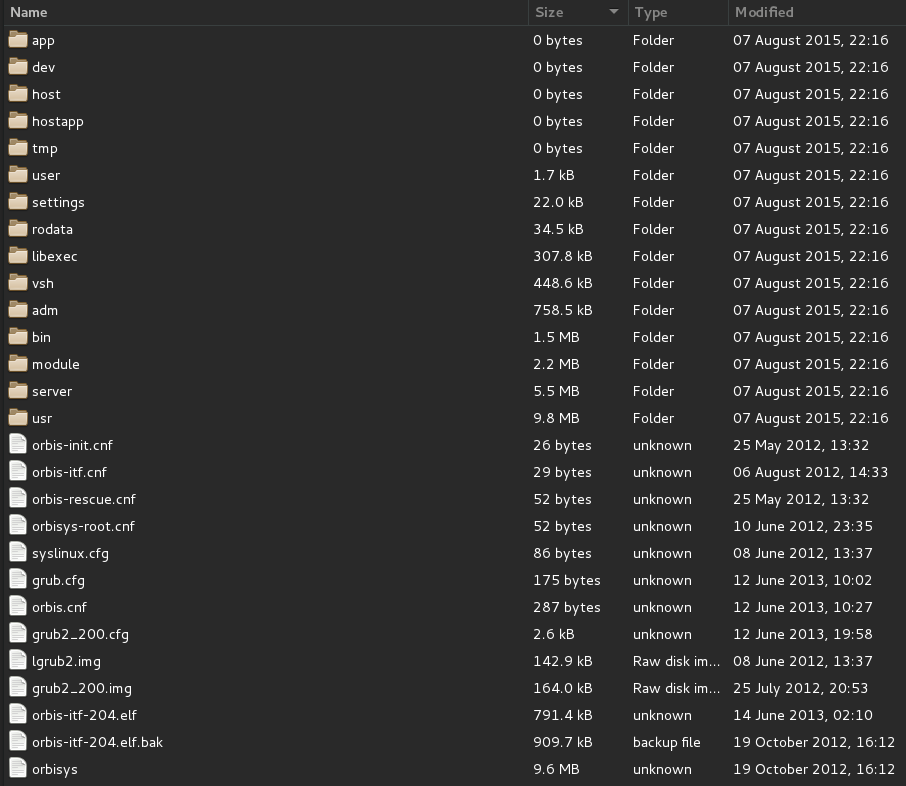
Finally, GregoryRasputin posted a screenshot of a PS4 Filesystem Root Dump with details below, which has been confirmed by PlayStation 4 developer Lucif3r as follows:
From GregoryRasputin: Christmas is a time for loving and sharing, it is about spending time with the family and enjoying their company, which is why i am happy to let the PlayStationHaX family know that a little Christmas elf popped in to see me today and showed me something wonderful:
Of course with these being confidential Sony files, i cannot and will not link to any files. You can read about work into hacking the PS4, you can check these links:
For those wondering, yes, this was released today. Edited title to clear some things up a bit.
According to zecoxao regarding the PS4 dump: Apparently it's on a pastebin. Cleverly hidden...

If anyone runs across it, feel free to share it here... this way the entire PS4 scene can benefit from it rather than a limited number of people. 
Download: adm.rar / PS4 root dump (0.8.2) + kernel / NPXX51150_TEST_APP_HELLO_WORLD_0.01_[DEBUG].rar (27.9 MB) via eXtreme-Modding.de
Merry Christmas
Here's all the patches you need for fuse to run on 5.05 retail via Pastebin.com:
M.e.M.e is ps4 filesystem case sensitive ? \ph\source\data\Menu\Movies\ Vs. \ph\source\data0.pak\menu\movies\  maybe potentional problem backporting DL2 for 5.05
maybe potentional problem backporting DL2 for 5.05 

From Wololo: Zecoxao, who's very close to the PS3/PS4 dev scene, shared a screenshot on Twitter, showing some reverse engineering work on what appears to be PS4 system files:
From GregoryRasputin: Christmas is a time for loving and sharing, it is about spending time with the family and enjoying their company, which is why i am happy to let the PlayStationHaX family know that a little Christmas elf popped in to see me today and showed me something wonderful:
Of course with these being confidential Sony files, i cannot and will not link to any files. You can read about work into hacking the PS4, you can check these links:
For those wondering, yes, this was released today. Edited title to clear some things up a bit.
According to zecoxao regarding the PS4 dump: Apparently it's on a pastebin. Cleverly hidden...
Download: adm.rar / PS4 root dump (0.8.2) + kernel / NPXX51150_TEST_APP_HELLO_WORLD_0.01_[DEBUG].rar (27.9 MB) via eXtreme-Modding.de
Merry Christmas
Here's all the patches you need for fuse to run on 5.05 retail via Pastebin.com:
Code:
//suser_enabled in priv_check_cred
ksuser_enabled=1;
//add jail friendly for fuse file system
p->vfc_flags=0x00400000 | 0x00080000;
//avoid enforce_dev_perms checks
//kfuse_enforce_dev_perms=0;
//default prison_priv_check to 0
kernel_ptr[0x3B219E]=0;
//skip devkit/testkit/dipsw check in fuse_loader
kernel_ptr[0x49DDDE] = 0xEB;
kernel_ptr[0x49DDDF] = 0x1B;
//skip sceSblACMgrIsSyscoreProcess check in fuse_open_device
kernel_ptr[0x4A28EE] = 0xEB;
kernel_ptr[0x4A28EF] = 0x0;
//skip sceSblACMgrIsDebuggerProcess/sceSblACMgrIsSyscoreProcess check in fuse_close_device
kernel_ptr[0x4A29E2] = 0xEB;
//skip sceSblACMgrIsDebuggerProcess/sceSblACMgrIsSyscoreProcess check in fuse_poll_device
kernel_ptr[0x4A2F34] = 0xEB;
// skip sceSblACMgrIsSyscoreProcess check in fuse_vfsop_mount
kernel_ptr[0x4A30F7] = 0xEB;
kernel_ptr[0x4A30F8] = 0x04;
// skip sceSblACMgrIsMinisyscore/unknown check in fuse_vfsop_unmount
kernel_ptr[0x4A384C] = 0xEB;
kernel_ptr[0x4A384D] = 0x00;
// skip sceSblACMgrIsSystemUcred check in fuse_vfsop_statfs
kernel_ptr[0x4A3BED] = 0xEB;
kernel_ptr[0x4A3BEE] = 0x04;
the fcking eperm was in fuse_device_open xD
