Proceeding the PS5 BD-JB ELF Loader v1.2 revision, 'twas the night before Christmas and based on John Tornblom's continued Github Repository updates @ifcompass (Ifaicompa via Twitter) made available a system-mount.elf R/W payload to Read / Write to PlayStation 5's /system partition for those in the PS5Scene using the previously released PS5 IPV6 Kernel Exploit. 
Ifaicompa notes the following details on Twitter, to quote:
(❁´◡`❁) Merry Christmas everyone
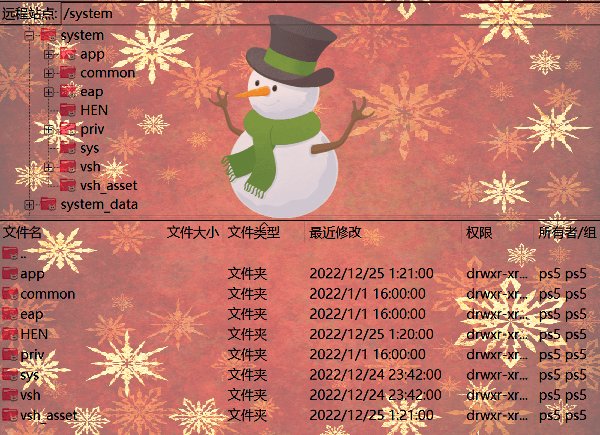
 This payload will Remount /system with write permissions
This payload will Remount /system with write permissions
 It can only be loaded via the BD-JB ELF Loader!
It can only be loaded via the BD-JB ELF Loader!
 After loading, load FTPS5 via Webkit, FTP will have system R/W
After loading, load FTPS5 via Webkit, FTP will have system R/W
 Thanks John Tornblom
Thanks John Tornblom
 Warning: If you delete files in /system at will, it may cause PS5 to become a brick!
Warning: If you delete files in /system at will, it may cause PS5 to become a brick! 
 For those who prefer visual explanations: FAFO
For those who prefer visual explanations: FAFO 
From Pastebin.com: nmount PS5 system rw source from decompiler
Mr. Nasu, who made a payload that enables writing of the PS5 system, seems to be making a payload that can read and write not only the system but all layers. Thankfully I am a tester.
lol, the reason why mounting the system partitions is only possible in bd-jb (and also in the ps4 ps2 emulator, if a kernel exploit eventually shows for ps5 on 6.50+) is because both of these systems use libkernel_sys, which supports nmount. neither _web nor regular libkernel do
goes without saying to those who purchased a digital ps5: you won't have any fun making permanent changes on your console
nobody bought the exploitable game at that time (cturt had not revealed it yet)
you will, you just won't be able to do perma mods until there is a hv exploit
it doesn't work without privs
Ifaicompa notes the following details on Twitter, to quote:
(❁´◡`❁) Merry Christmas everyone
- ELF download: system-mount.elf (10 KB)
From Pastebin.com: nmount PS5 system rw source from decompiler
Code:
__int64 __fastcall _payload_base(_QWORD *arrayPointer, unsigned int *lengthPointer, __int64 string1, __int64 string2)
{
__int64 functionResult; // rax
_QWORD *str1Ptr; // rbx
__int64 strdupStr2; // rax
__int64 strlenStr2; // rax
int v10; // [rsp+2Ch] [rbp-14h]
int v11; // [rsp+2Ch] [rbp-14h]
functionResult = *lengthPointer;
if ( (int)functionResult >= 0 )
{
v10 = *lengthPointer;
*arrayPointer = realloc(*arrayPointer, 16LL * (int)(*lengthPointer + 2));
if ( *arrayPointer )
{
str1Ptr = (_QWORD *)(*arrayPointer + 16LL * v10);
*str1Ptr = strdup(string1);
*(_QWORD *)(*arrayPointer + 16LL * v10 + 8) = strlen(string1) + 1;
v11 = v10 + 1;
if ( string2 )
strdupStr2 = strdup(string2);
else
strdupStr2 = 0LL;
*(_QWORD *)(*arrayPointer + 16LL * v11) = strdupStr2;
if ( string2 )
strlenStr2 = strlen(string2) + 1;
else
strlenStr2 = 0LL;
*(_QWORD *)(*arrayPointer + 16LL * v11 + 8) = strlenStr2;
functionResult = (__int64)lengthPointer;
*lengthPointer = v11 + 1;
}
else
{
*lengthPointer = -1;
return perror("realloc");
}
}
return functionResult;
}
int __cdecl main(int argc, const char **argv, const char **envp)
{
unsigned int v4; // [rsp+4h] [rbp-Ch] BYREF
__int64 v5; // [rsp+8h] [rbp-8h] BYREF
v5 = 0LL;
v4 = 0;
_payload_base(&v5, &v4, (__int64)"fstype", (__int64)"exfatfs");
_payload_base(&v5, &v4, (__int64)"fspath", (__int64)"/system");
_payload_base(&v5, &v4, (__int64)"from", (__int64)"/dev/ssd0.system");
_payload_base(&v5, &v4, (__int64)"large", (__int64)"yes");
_payload_base(&v5, &v4, (__int64)"timezone", (__int64)"static");
_payload_base(&v5, &v4, (__int64)"async", 0LL);
_payload_base(&v5, &v4, (__int64)"ignoreacl", 0LL);
if ( !(unsigned int)nmount(v5, v4, 0x10000LL) )
return 0;
perror("nmount");
return 1;
}lol, the reason why mounting the system partitions is only possible in bd-jb (and also in the ps4 ps2 emulator, if a kernel exploit eventually shows for ps5 on 6.50+) is because both of these systems use libkernel_sys, which supports nmount. neither _web nor regular libkernel do
goes without saying to those who purchased a digital ps5: you won't have any fun making permanent changes on your console
nobody bought the exploitable game at that time (cturt had not revealed it yet)
you will, you just won't be able to do perma mods until there is a hv exploit
it doesn't work without privs

