All day PS4 dev @ryan111 (PS4Work Blog updates from him HERE and HERE) has been working on a PlayStation 4 4.0 jailbreak, and has come across a "command" in the web browser about: that gives you info about it.
Which reads:
Now i did some research on this and this is what i came up with.
https://user-agents.me/useragent/mozilla50-macintosh-intel-mac-os-x-10_9_4-applewebkit537782-khtml-like-gecko-version706-safari537782
Which is about the WebKit and:
https://www.cvedetails.com/vulnerability-list/vendor_id-452/product_id-3264/version_id-112576/Mozilla-Firefox-5.0.html
Which are vulnerabilities for Mozilla 5.0.
Now im not sure if this has already been found but this is the first of me hearing it. Wanted to post this for people so they could know devs are working on a 4.0 JB and never give up hope.
Finally, below are some related Tweets from PlayStation 4 developer CTurt and the ReadMe file from the work-in-progress PS4 Playground 4.00 GIT via darkslake, to quote:
PS4 4.00 Unsigned Code Execution
This GitHub Repository contains all the necessary tools for getting PoC Unsigned Code Execution on a Sony PS4 System with firmwares 3.15, 3.50, 3.55 and 4.00-exploit-ps4.
This Exploit, is based-off Henkaku's WebKit Vulnerability for the Sony's PSVita. It includes basic ROP and is able to return to normal execution.
Pre-Requisites:
There are two different methods to execute the Exploit, but first let's clarify how we will know which one to use. If your PlayStation 4 has got an already set-up PlayStation Network Account on it, you should use method 1.
Else, if your PlayStation 4 -NEVER- had a PlayStation Network Account on it, you should use method 2. Probably you will ask why, it's pretty much easy to explain and understand:
When you buy a PS4, comes unactivated, meaning that nobody has entered SEN Account on it. (Method 2) Once you use a SEN Account on it, the PS4 becomes an activated console. (Method 1) This doesn't affect the actual payload, but you should take in mind which method use.
Method 1:
Run this command on the folder you've downloaded this repo:
All the debug options will be outputted during the Exploit process. Navigate to your PS4's Web Browser and simply type on the adress bar, your PC's IP Adress. Wait until the exploit finishes, once it does, PS4 will return to it's normal state. An example of what will look like found HERE.
Method 2:
A dns.conf file which is present on the source, needs to be edited accordingly your local PC's IP Address. PlayStation 4's DNS Settings must be changed in order to point the PC's IP Address where the Exploit is located. Once you've edited the dns.conf file, simply run the next command on the folder where you downloaded this repo:
And then:
All the debug options will be outputted during the Exploit process. Once Python part is done, get into your PlayStation 4, navigate to the User's Guide page and wait until exploit finishes out. An example of what will look like found HERE.
Miscellaneous:
If you want to try the socket test, change the IP Address located at the bottom of the ps4sploit.html file with your computer's one and run this command:
You should see something like:
Notes about this exploit:
xyz - Much of the code is based off of his code used for the Henkaku project
Anonymous contributor - WebKit Vulnerability PoC
CTurt - I basically copied his JuSt-ROP idea
xerpi - Used his idea for the socket code
rck`d - Finding bugs such as not allocating any space for a stack on function calls
Maxton - 3.50 support and various cleanup
Thunder07 - 3.15 support darkslake - 4.00 support and various cleanup
Contributing
The code currently is a bit of a mess, so if you have any improvements feel free to send a pull request or make an issue. Also I am perfectly fine if you want to fork and create your own project.
final-4.00-exploit-ps4
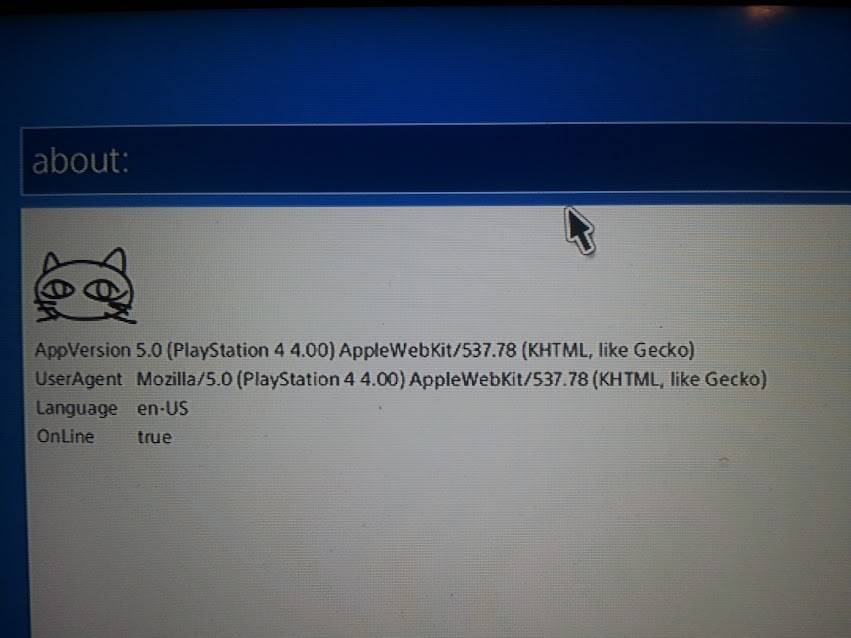
Which reads:
Code:
AppVersion 5.0 (Playstation 4 4.00) AppleWebKit/537.78 (KHTML, like Gecko)
UserAgent Mozilla/5.0 (Playstation 4 4.0) AppleWebKit/537.78 (KHTML, like Gecko)
Language en-US
OnLine truehttps://user-agents.me/useragent/mozilla50-macintosh-intel-mac-os-x-10_9_4-applewebkit537782-khtml-like-gecko-version706-safari537782
Which is about the WebKit and:
https://www.cvedetails.com/vulnerability-list/vendor_id-452/product_id-3264/version_id-112576/Mozilla-Firefox-5.0.html
Which are vulnerabilities for Mozilla 5.0.
Now im not sure if this has already been found but this is the first of me hearing it. Wanted to post this for people so they could know devs are working on a 4.0 JB and never give up hope.
Finally, below are some related Tweets from PlayStation 4 developer CTurt and the ReadMe file from the work-in-progress PS4 Playground 4.00 GIT via darkslake, to quote:
PS4 4.00 Unsigned Code Execution
This GitHub Repository contains all the necessary tools for getting PoC Unsigned Code Execution on a Sony PS4 System with firmwares 3.15, 3.50, 3.55 and 4.00-exploit-ps4.
This Exploit, is based-off Henkaku's WebKit Vulnerability for the Sony's PSVita. It includes basic ROP and is able to return to normal execution.
Pre-Requisites:
- A PC
- Running Windows, macOS or Linux
- A already set up basic server where the PS4 User's Guide launcher will point for loading the payload
- Python 2.7.X
- Python 3.X gives problems, since they included major changes on the syntax and on the libraries in comparison with 2.7
- A Sony PlayStation 4
- Running the following firmwares:
- 4.00
- Running the following firmwares:
- Internet Connection (PS4 and PC directly wired to the Router is the mostly preferred option)
There are two different methods to execute the Exploit, but first let's clarify how we will know which one to use. If your PlayStation 4 has got an already set-up PlayStation Network Account on it, you should use method 1.
Else, if your PlayStation 4 -NEVER- had a PlayStation Network Account on it, you should use method 2. Probably you will ask why, it's pretty much easy to explain and understand:
When you buy a PS4, comes unactivated, meaning that nobody has entered SEN Account on it. (Method 2) Once you use a SEN Account on it, the PS4 becomes an activated console. (Method 1) This doesn't affect the actual payload, but you should take in mind which method use.
Method 1:
Run this command on the folder you've downloaded this repo:
Code:
python server.pyMethod 2:
A dns.conf file which is present on the source, needs to be edited accordingly your local PC's IP Address. PlayStation 4's DNS Settings must be changed in order to point the PC's IP Address where the Exploit is located. Once you've edited the dns.conf file, simply run the next command on the folder where you downloaded this repo:
Code:
python fakedns.py -c dns.conf
Code:
python server.pyMiscellaneous:
If you want to try the socket test, change the IP Address located at the bottom of the ps4sploit.html file with your computer's one and run this command:
Code:
netcat -l 0.0.0.0 8989 -v
Code:
Listening on [0.0.0.0] (family 0, port 8989)
Connection from [192.168.1.72] port 8989 [tcp/sunwebadmins] accepted (family 2, sport 59389)
Hello From a PS4!- Currently, the exploit does not work 100%, but is around 80% which is fine for our purposes.
- Although it is confirmed to work, sometimes will fail, just wait some seconds and re-run the payload.
- Performing too much memory allocation after sort() is called, can potentially lead to more instability and it may crash more.
- The process will crash after the ROP payload is done executing.
- This is only useful for researchers. There are many many more steps needed before this becomes useful to normal users.
xyz - Much of the code is based off of his code used for the Henkaku project
Anonymous contributor - WebKit Vulnerability PoC
CTurt - I basically copied his JuSt-ROP idea
xerpi - Used his idea for the socket code
rck`d - Finding bugs such as not allocating any space for a stack on function calls
Maxton - 3.50 support and various cleanup
Thunder07 - 3.15 support darkslake - 4.00 support and various cleanup
Contributing
The code currently is a bit of a mess, so if you have any improvements feel free to send a pull request or make an issue. Also I am perfectly fine if you want to fork and create your own project.
final-4.00-exploit-ps4


