Proceeding the previous 7.02 PS4JB, the recent PS4 KHook Kernel Hooking Payload, updated PS4 FPKG Releases and Day[0] Stream earlier today PlayStation 4 Scene developer @sleirsgoevy (Github) made available via Twitter a PS4 7.50 Kernel Exploit noting with no promises that 7.55 may also come in a few more days as the exploit is confirmed working without any changes and released now! 
Download: 750.zip (508 KB) / todex.bin (For 7.55) (2.31 KB) / Live Demo via Chronoss09 / ps4jb-750-755.zip (511 KB) / PS4 Game Firmware Lists / 7.55 PS4 Games List / PS4 Official Firmware (OFW) Archives
It's always recommended to wait for improved stability and 7.50 payload ports before updating. In the Tweets below, he also stated the following details:
TEST new PS4 exploit 7.51 via donatelo27
TESTING 7.50 KERNEL EXPLOIT ON 7.51 via bilaltheking
Cheers to FLRIZDARKK for the heads-up earlier on and mohammad_fadel1 for sharing a screenshot via Twitter!
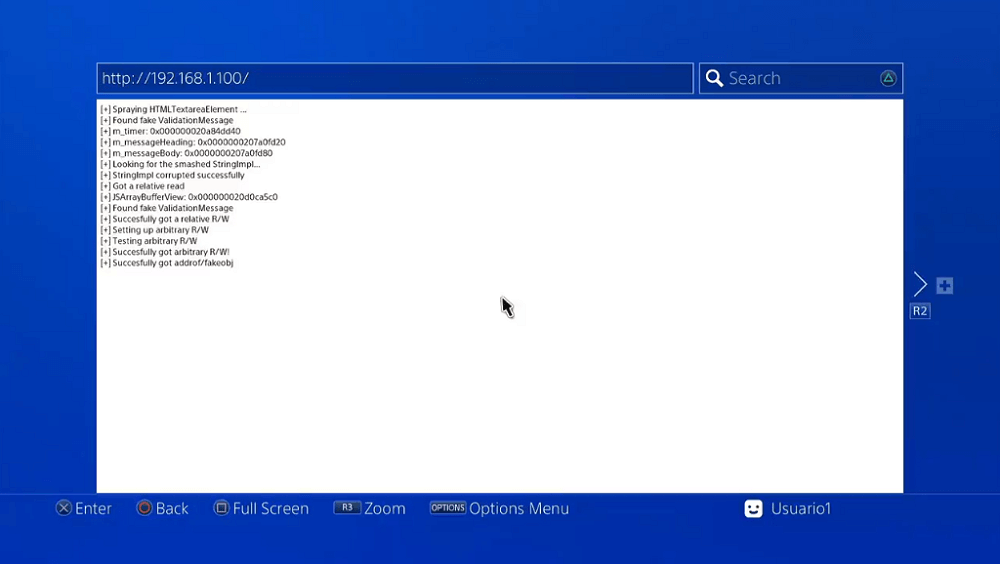
Download: 750.zip (508 KB) / todex.bin (For 7.55) (2.31 KB) / Live Demo via Chronoss09 / ps4jb-750-755.zip (511 KB) / PS4 Game Firmware Lists / 7.55 PS4 Games List / PS4 Official Firmware (OFW) Archives
It's always recommended to wait for improved stability and 7.50 payload ports before updating. In the Tweets below, he also stated the following details:
- 7.50, expects payload on 9020/tcp.
- Applied patches: mmap, mprotect, syscall everywhere, kexec, delayed panics.
- Note: there is no Mira/HEN for 7.50 yet!
Code:
// Patch sys_dynlib_dlsym: Allow from anywhere
int kpayload_dynlib_patch(struct thread *td, struct kpayload_firmware_args *args) {
UNUSED(td);
UNUSED(args);
void *kernel_base;
uint8_t *kernel_ptr;
uint8_t *kmem;
uint8_t *dynlib_patch_1;
uint8_t *dynlib_patch_2;
kernel_base = &((uint8_t *)__readmsr(0xC0000082))[-0x000001C0];
kernel_ptr = (uint8_t *)kernel_base;
dynlib_patch_1 = &kernel_ptr[0x004523C4];
dynlib_patch_2 = &kernel_ptr[0x00029A30];
uint64_t cr0 = readCr0();
writeCr0(cr0 & ~X86_CR0_WP);
kmem = (uint8_t *)dynlib_patch_1;
kmem[0] = 0x90;
kmem[1] = 0xE9;
kmem = (uint8_t *)dynlib_patch_2;
kmem[0] = 0x48;
kmem[1] = 0x31;
kmem[2] = 0xC0;
kmem[3] = 0xC3;
writeCr0(cr0);
return 0;
}
int dynlib_patch() {
struct kpayload_firmware_info kpayload_firmware_info;
kpayload_firmware_info.fw_version = 0;
return kexec(&kpayload_dynlib_patch, &kpayload_firmware_info);
}TESTING 7.50 KERNEL EXPLOIT ON 7.51 via bilaltheking
Cheers to FLRIZDARKK for the heads-up earlier on and mohammad_fadel1 for sharing a screenshot via Twitter!



