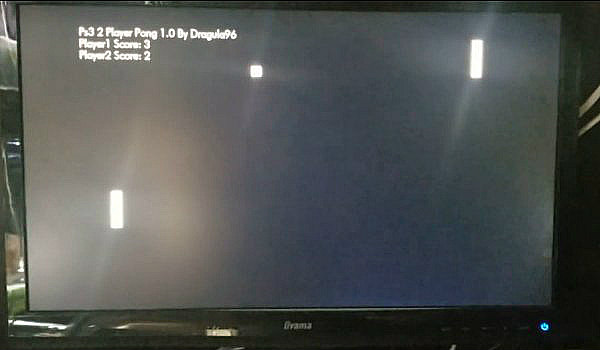
Since last week's PS4 Blu-ray Disc Java Sandbox Escape and the corresponding PS5 BD-JB Exploitation, scene developer @yyoossk (Cloud0835 on Twitter) shared on his Yyoossk.Blogspot.com page a demonstration video showcasing PS5 BD-J with the homebrew game PS3 2 Player Pong 1.0 By Dragula96 from Yyoossk's YouTube Channel that was since repacked by @SocraticBliss (Twitter) via Discord as a test. 
Download: PS3_Pong_Ready_to_Go_Pack.rar (80.4 KB)
 As noted by KameleonRe on Twitter, "this is not the actual exploit... it's just testing a Java app under BD-J."
As noted by KameleonRe on Twitter, "this is not the actual exploit... it's just testing a Java app under BD-J."
Here's a brief guide for those in the PS5Scene from his PS4 & PS5 Blu-ray Java Test page, roughly translated below:
PS5 BDJ Test
Download: PS3_Pong_Ready_to_Go_Pack.rar (80.4 KB)
Here's a brief guide for those in the PS5Scene from his PS4 & PS5 Blu-ray Java Test page, roughly translated below:
I tested Blu-ray Java released the other day with PS4 & PS5.
- Insert a BD-RE disc that can be written many times (or a BD-R disc that can be written only once) into the PC.
- Download & unzip the PS3_Pong_Ready_to_Go_Pack.rar file created by Socratic Bliss
- Rename INDEX.BDM in the AVCHD / BDMV folder to index.bdmv and MOVIEO BJ.BDM to MovieObject.bdmv
- Download and install ImgBurn from the link below and start it:
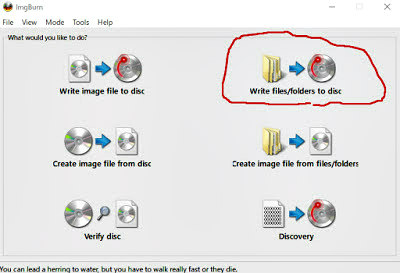
- Write files / folders to disc:
- Click the folder icon and select the AVCHD folder.
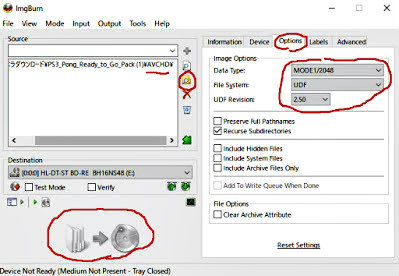
- Write if UDF is set to 2.50 on the Options tab.
- Just boot the burned disc.
PS5 BDJ Test

