Following my previous guide, here is another tutorial as requested covering how to add your choice of payload into PS4 playground for ESP8266.
Again I use treyjazz's sample webpage for this tutorial (in 'data' folder inside PS4Exploit).
So how you add the payload of your choice?

My brain just stopped functioning right now.



Again I use treyjazz's sample webpage for this tutorial (in 'data' folder inside PS4Exploit).
- I suggest you download Notepad++ for code editing. Download and install.
- So now navigate to 'data' folder. You will see bunch of files (.js and .html) in it. The webpage you see on ESP8266 is coded in 'index.html'. So find 'index.html', right-click on it, click 'Edit with Notepad++'.
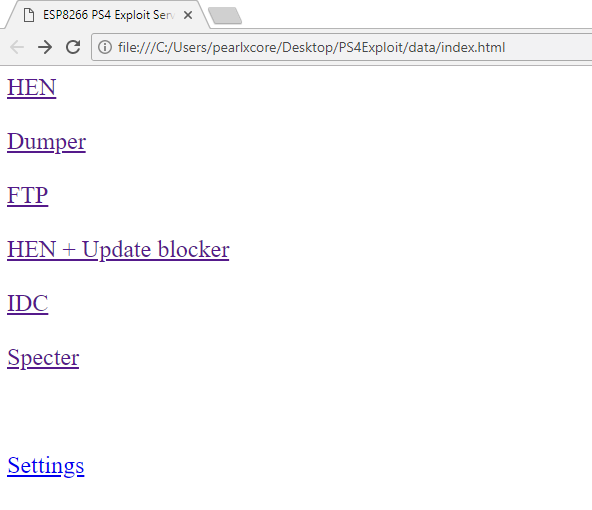
- Now double-click on 'index.html' and the page will open on your browser.
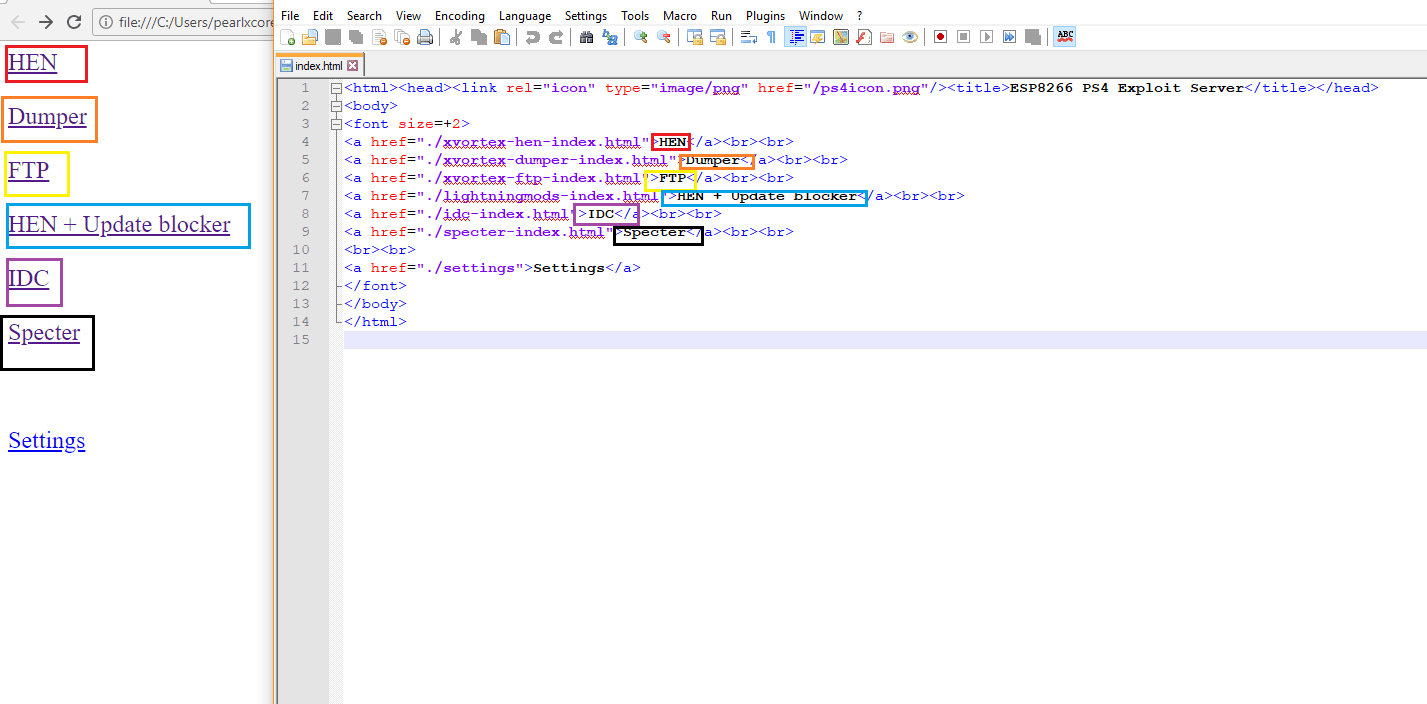
- Now compare side by side the code and the webpage
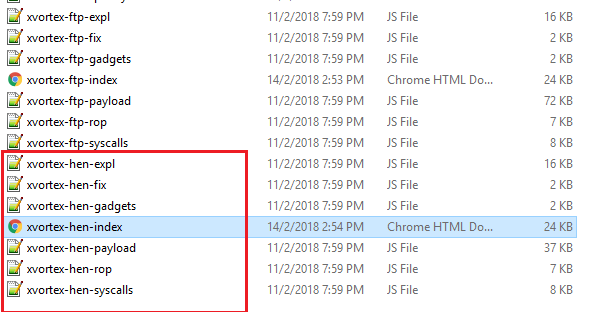
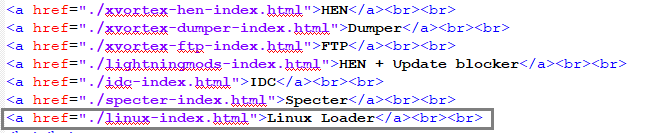
- You can now understand a bit the how its relate. In the code, those I highlighted in colour is the text showed in webpage. Each payload option has different index source. For example HEN is pointed to 'xvortex-hen-index.html'. So now find 'xvortex-hen-index.html' in the folder.
- You will see files with same name 'xvortex-hen-'. Those are the HEN exploit files required to exploit your PS4. And you see files with other name too
- The different name separate the exploit files so its not mix up.
- Ok back to our example, HEN exploit. Right-click on 'xvortex-hen-index.html' and scroll down to bottom.
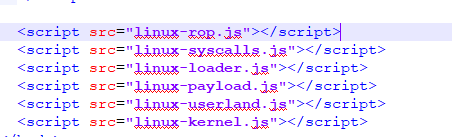
- You can see some .js file mention in the code. It means the webpage calling the .js file during the execution of exploit. Each of payload type have it files to excute.
Code:
index.html
|
| (When you selected HEN)
|
xvortex-hen-index.html
|
| (calling)
|
|-------------------------------
|xvortex-hen-expl.js |
|xvortex-hen-gadgets.js |
|xvortex-hen-rop.js |
|xvortex-hen-payload.js |
--------------------------------
|
|
HEN exploit done- 1st prepare the exploit files for example you want to add. For example you want to add Linux Loader payload
- Let say you already have Linux payload and other files
- To prevent from files mixing up, rename the files
- Open 'linux-index.html' with Notepad++ and scroll to bottom. Insert the all .js files required for the exploit and save it.
- Now open 'index.html' with Notepad++ and now we add new payload option in webpage and save it.
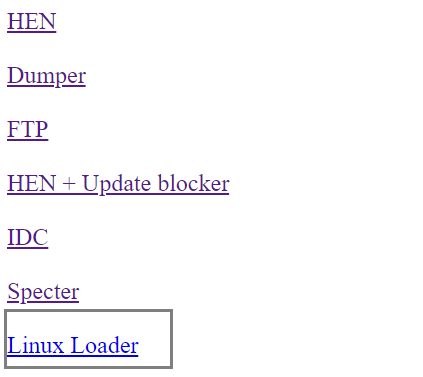
- To test our webpage, simply double-click 'index.html' to view the webpage
- We have new payload option for Linux Loader
My brain just stopped functioning right now.

