This is an update to my Android app to host the PS4 5.0X exploit and payloads.
This initial release just contains the 3 main payloads.
To use it you have to setup a wifi hotspot with your phone/tablet and connect the PS4 to that hotspot or connect the phone/tablet to the same network the PS4 is on.
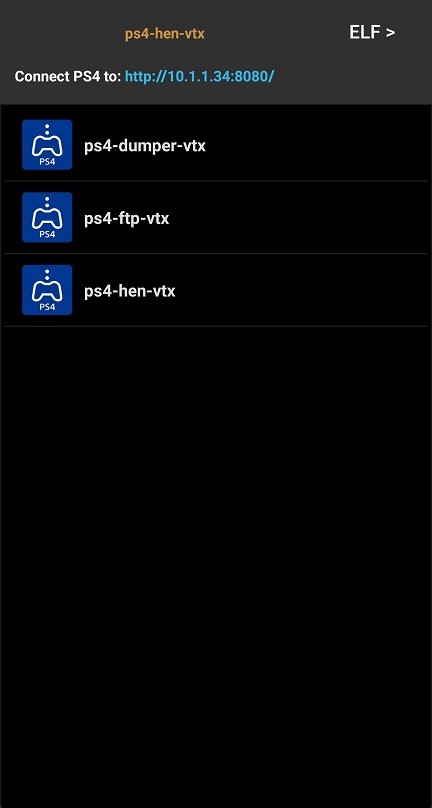
Then install the app and open it and at the top will be the address you need to connect to with the PS4.
Your device might ask you about installing an application from "unknown sources" this is ok to allow, it just means its not coming from Google Play.
You just select the payload you want to run in the app and then use the PS4 to goto the address that you see in the app.
To change the payload just select it in the app and then use the ps4 to revisit/refresh the address again.
you can add more payloads to the app you just plug your phone into your computer and copy any payload BIN file you like into the PS4_50X_Payloads directory.
you will get one "There is not enough free system memory" because that's how this exploit works, just click ok and the page should reload and load the selected payload.
Download:
ps4_serve3_v2_3.zip / GIT
Spoiler: Depreciated
Eye candy:
Install GTA 5 mod menu 5.05 PS4 with android app, wildemodz
This initial release just contains the 3 main payloads.
To use it you have to setup a wifi hotspot with your phone/tablet and connect the PS4 to that hotspot or connect the phone/tablet to the same network the PS4 is on.
Then install the app and open it and at the top will be the address you need to connect to with the PS4.
Your device might ask you about installing an application from "unknown sources" this is ok to allow, it just means its not coming from Google Play.
You just select the payload you want to run in the app and then use the PS4 to goto the address that you see in the app.
To change the payload just select it in the app and then use the ps4 to revisit/refresh the address again.
you can add more payloads to the app you just plug your phone into your computer and copy any payload BIN file you like into the PS4_50X_Payloads directory.
you will get one "There is not enough free system memory" because that's how this exploit works, just click ok and the page should reload and load the selected payload.
Download:
ps4_serve3_v2_3.zip / GIT
Spoiler: Depreciated
Eye candy:
Install GTA 5 mod menu 5.05 PS4 with android app, wildemodz


