As mentioned previously, following Fail0verflow's Documentation, the PS4 NoBD Updating Method, his PS4 Updater Toolkit release and the PS4 RL78 Syscon implementation PlayStation 4 scene developer @theorywrong shared via Twitter a new post on his blog at TheoryWrong.me detailing his research with the PS4 Update Tool known as OrbisSWU discussing PS4 NoBD, downgrading and how updates work. 
 Feel free to support his continued work on his Patreon Page, and here's a rough translation via Google of his Latest Blog Article for those feeling a bit techy today: OrbisSWU, the PS4 update tool.
Feel free to support his continued work on his Patreon Page, and here's a rough translation via Google of his Latest Blog Article for those feeling a bit techy today: OrbisSWU, the PS4 update tool.
Hello !
Here is finally the 1st article for the PS4 in relation to my work!
 Note: Some points may be vague, it is not easy to understand a complex system like that, but I will try to transcribe the exact operation.
Note: Some points may be vague, it is not easy to understand a complex system like that, but I will try to transcribe the exact operation.
Today we are going to talk about the “OrbisSWU” tool which manages the PS4 update system.
Controlled PS4 update
OrbisSWU is a special application stored in all PUPs on the PS4. It allows updating the firmware of the PS4. Kernel, Application, Blueray Reader and WiFi / Bluetooth Chipset. Everything goes through him.
It all starts in the SceShellUI, when your PS4 requests to do an update, it will start by recovering it in a specific folder. Luckily. SceShellUI is an application that actually loads a C # coded .exe (yes, yes) based on Mono. This library is called app.exe.sprx.
It will suffice to recover this library from the FTP of xVortex (which has the particularity of decrypting executables from PS4 to ELF). Then extract the Windows executable.
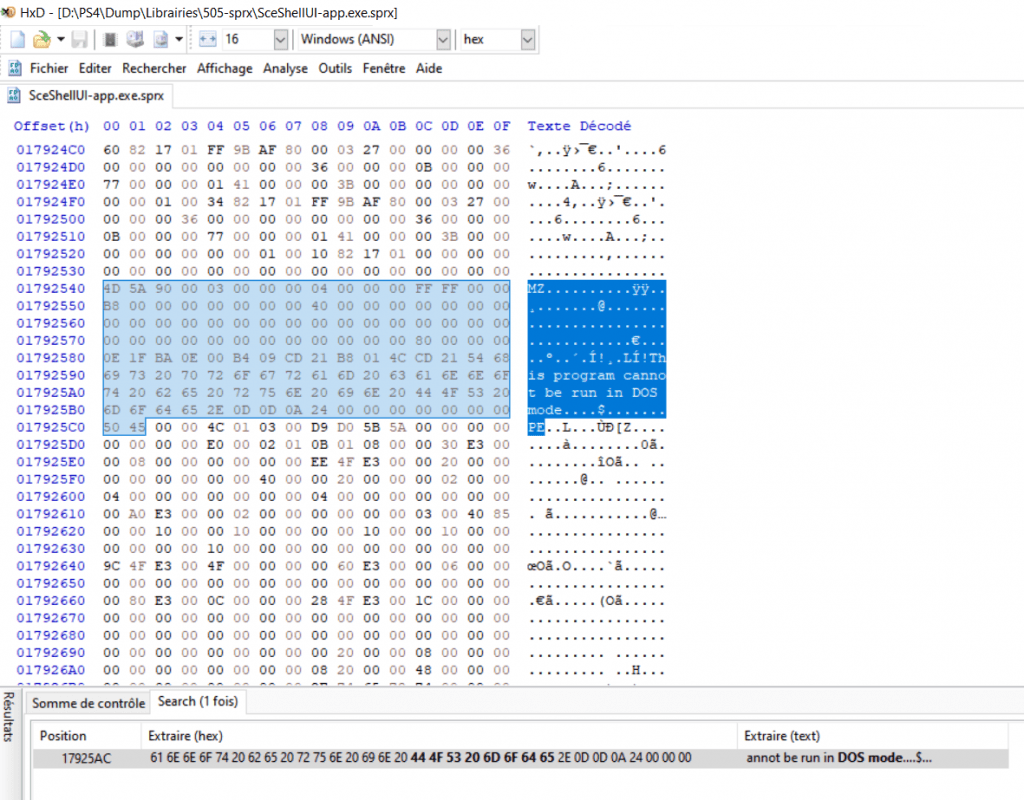
Hexadecimal view of the PS4 library containing the executable
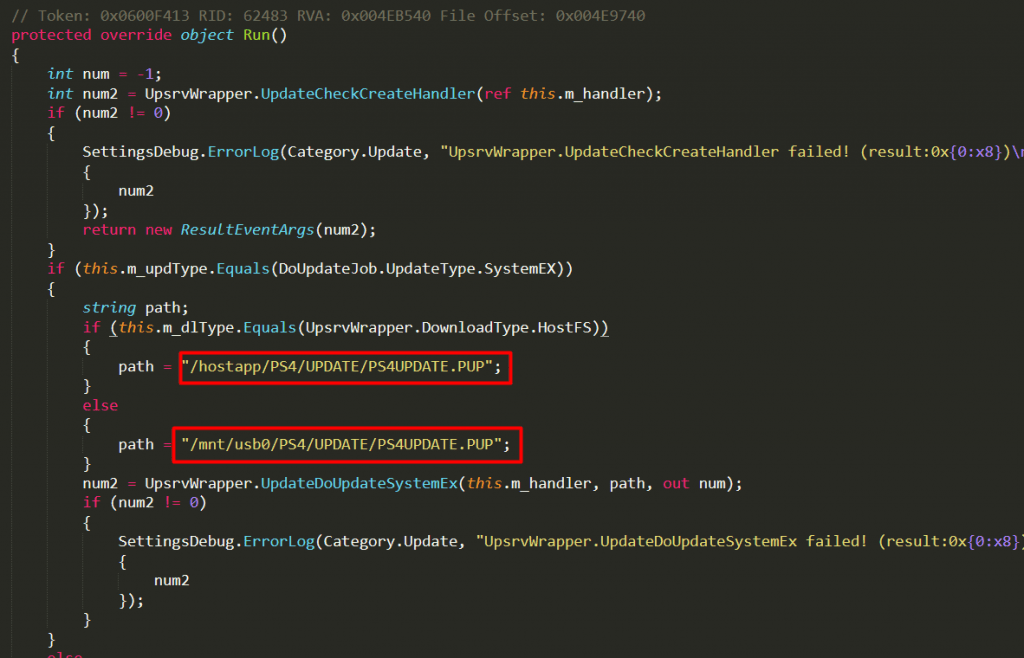
DoUpdateJob.cs in app.exe.sprx
The SceShellUI will copy the PUP into space /update/PS4UPDATE.PUP and extract the orbis_swu.elf. Then, a restart in update mode will be initiated.
During startup, the mini-syscore (process 1 after loading the kernel) will check in which mode it should be loaded.
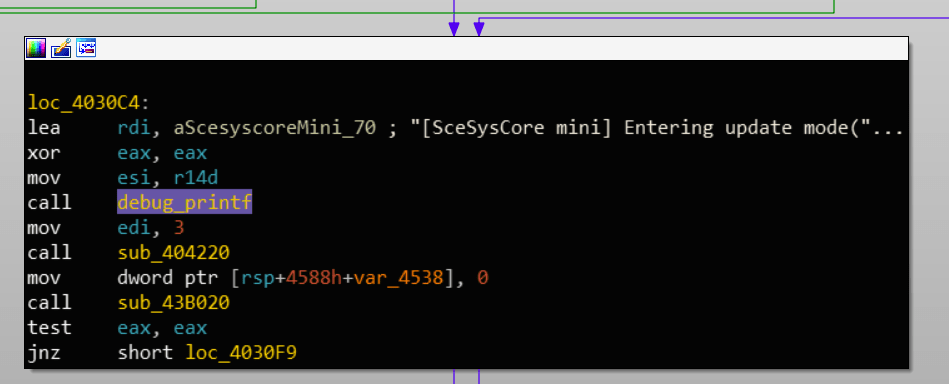
The mini-syscore checks which mode it should load when starting the console, here the "update" mode.
Once the update mode is initiated, the executable orbis_swu.self previously extracted will be executed by the console by means of the sc_spawn function.
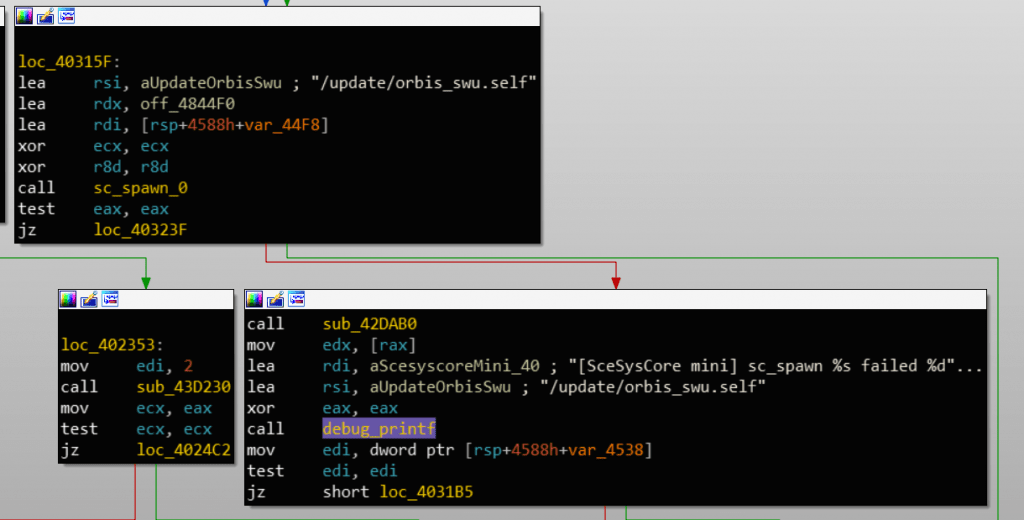
Launch of orbis_swu.self from mini-syscore using update mode
During its execution, the PUP will be fully decrypted. PUPs are update files made up of “blobs”, encrypted parts, sometimes compressed which will be decrypted one by one by the SAMU (The security processor of the PlayStation 4).
A list of blobs for Firmware 5.05, here the signature is in md5 and corresponds to the encrypted version. The content of the files is decrypted.
The blobs between them form different types of files, here is a (small) list of files that we can find inside:
1, ???, / dev / sflash0s0x32b
2, ???, / dev / sflash0s0x33
3, ???, / dev / sflash0s0x38
3, ???, wlan_firmware.bin
4, ???, / dev / sflash0s1. cryptx2b
5, secure_modules.bin, /dev/sflash0s1.cryptx3b
6, system.img, /dev/da0x4b.crypt
7, ???, / dev / da0x2
8, eap.img, /dev/da0x3.crypt
9, recovery .img, /dev/da0x0.crypt
10, /dev/sflash0s1.cryptx40
11, /dev/da0x1.crypt
11, preinst.img
12, system_ex.img, /dev/da0x5b.crypt
13, / dev / sflash0s0x32b
14, / dev / sflash0s0x33
To decrypt the PUP, the PS4 will use a command list (ioctl) for the "device" /dev/pup_update0:
It should be noted that the SAMU (Security Coprocessor) refuses to decrypt PUPs of version lower than the current version, it is one of the security mechanisms which detects attempts to downgrade.
Once the songs have been decrypted, Orbis_SWU will use specialized functions to update the different parts of the console, such as the BlueRay player, the Wifi / Bluetooth chipset, etc.
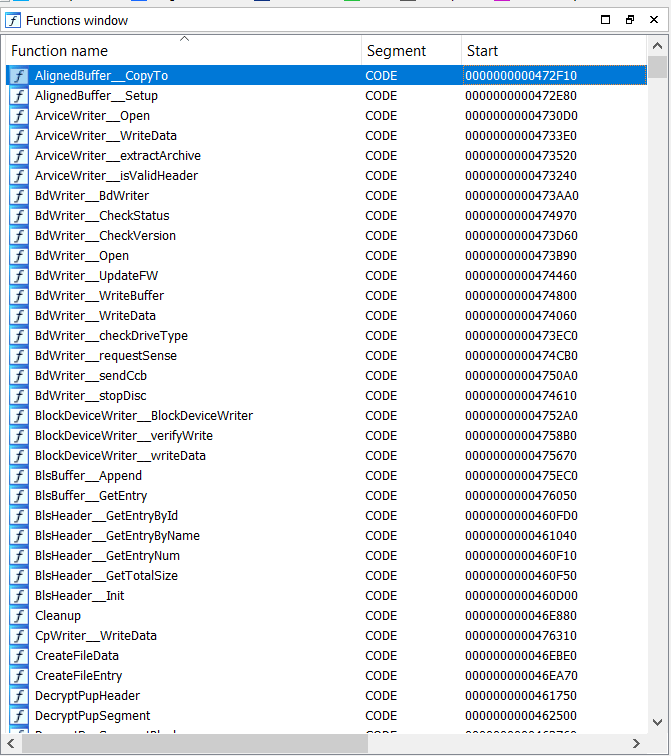
A small part of the functions of orbis_swu.self
Launching the update outside of Update Mode
It is possible to launch the update utility without putting the console in update mode, it can still update the components of the PS4. To do so, you need a Kernel exploit, the H (omebrew) EN (abler), and the make_fself.py of Flat_Z
The idea is that through a Homebrew "Hosts", to execute a modified orbis_swu.self which will do what we want. Just use the function
The modification of the orbis_swu will have to apply 2 patches to make it usable with a host application.
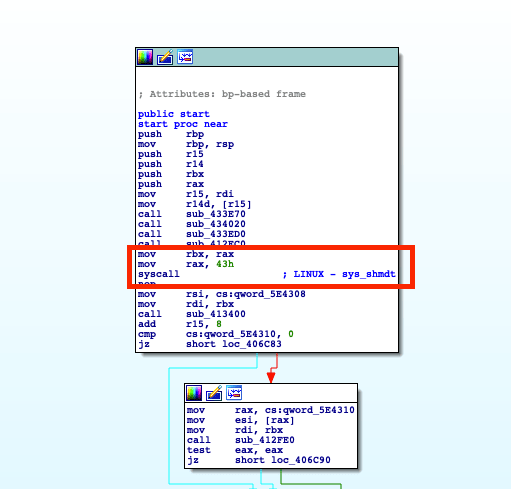
Modification of the "start" to execute a syscall (here 67) which will simply delete the sandbox from the application.
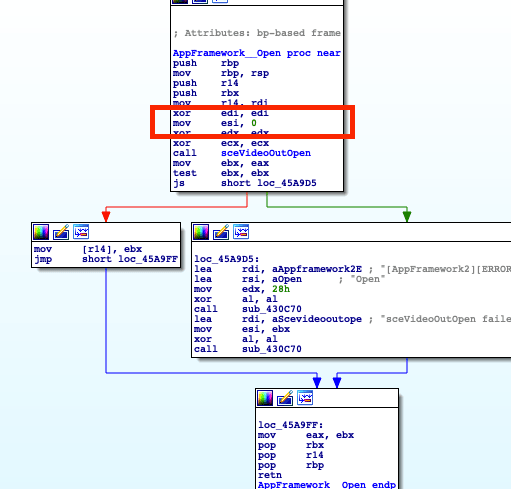
Here, the ESI register (Argument 2) must be set to 0 to set it to MAIN
Once this is done, your homebrew is ready to use the orbis_swu to perform updates! Now is when things start to get interesting!
The orbis_swu.self launched without the presence of an update.
Case 1: Update a PS4 without Blu-ray player
The first possible use of this is to bring in the update of consoles without Blu-ray player possible.
Here we can see that the update is impossible because the function
find the Blu-ray player. It would be enough to modify this function to launch an update to a higher firmware.
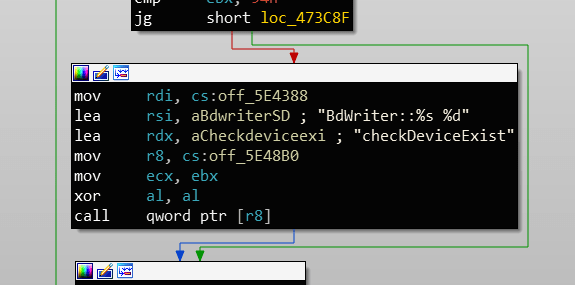
The location of the error display
The patch will be very simple, it will suffice to modify the instruction to return the error with a
instead of a
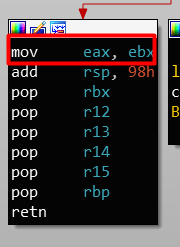
The instruction to modify
Tadaaaa! PS4 updates even without Blu-ray player
 WARNING ! Updating your PS4 without a Blu-ray player is not without risk without a hard drive backup, you will no longer be able to use the restoration tools (Soft Brick). It will always be possible to add a Blu-ray player to unblock the situation.
WARNING ! Updating your PS4 without a Blu-ray player is not without risk without a hard drive backup, you will no longer be able to use the restoration tools (Soft Brick). It will always be possible to add a Blu-ray player to unblock the situation.
PS4 update without being in update mode
Case 2: Downgrade attempt
Even if it may seem fanciful to try to downgrade in the simplest way possible, it is still necessary that this process recalls the downgrade of the PSVita Modoru by TheFlow which runs its update module to downgrade with a modified version.
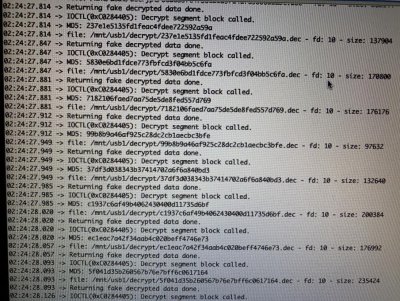
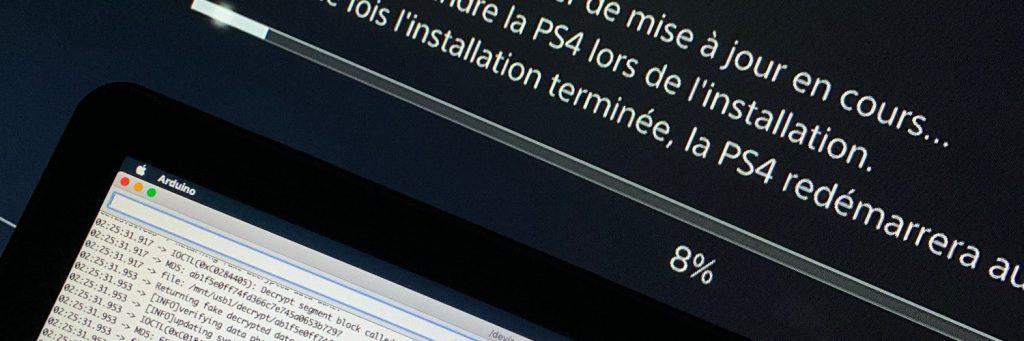
Here the idea is simple, if the PS4 cannot decrypt blobs of PUP lower than its version, we will decrypt them for him. The attack is simple, we will hook (hook) the syscall dedicated to ioctl and intercept the calls made to the "device" of decryption then:
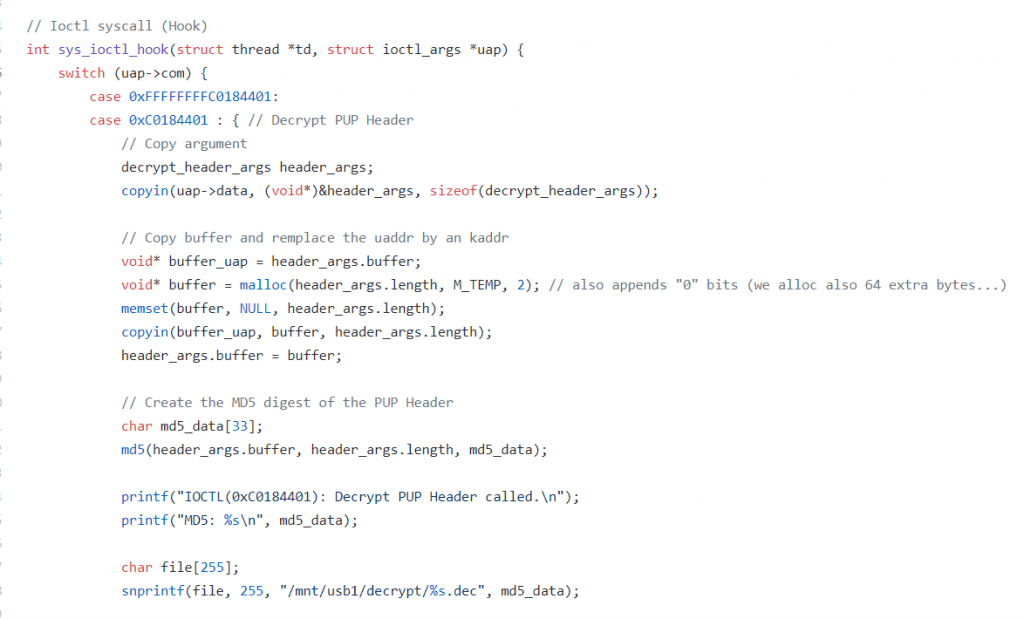
"Ioctl" syscall hook is hooking useful functions.
Once this was in place, I was surprised that it worked! The PS4 has accepted the update!
However, an error at the Switch Bank level. Which cancels the update and switches back to the current version (The backup bank)
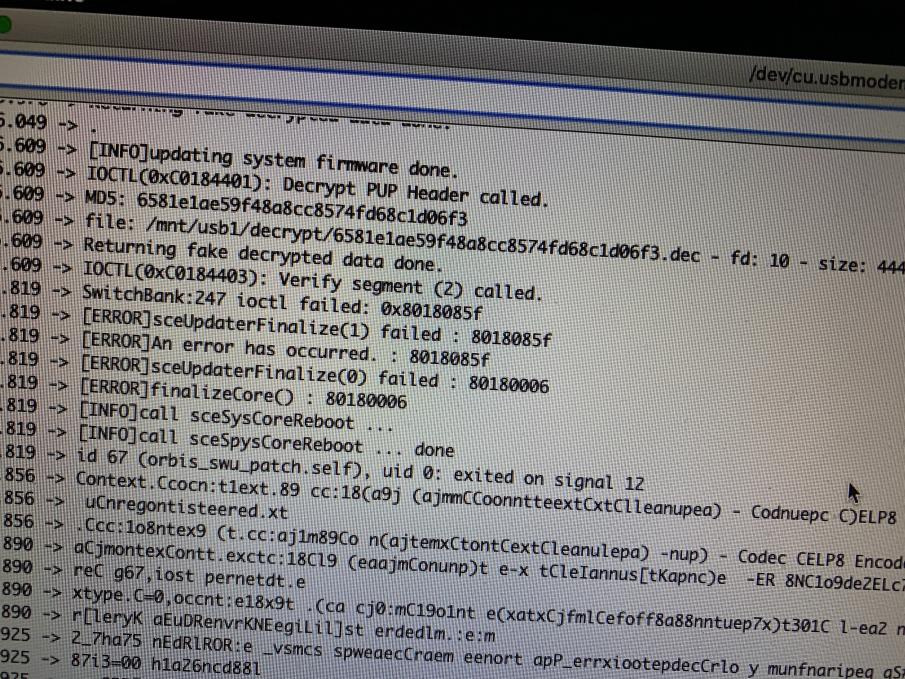
Error 0x8018085F (SCE_UPDATER_CORE_ERROR_PUP_US_NEEDAUTH)
After analysis of the SFLASH, it is possible to notice that values have all the same changed, such as the version of this one.
I continue my research to know how to correct the switch bank and why not have the possibility of Downgrade ^^
I hope that the article will have you more, I continue my work. Ciao!
Source:
Hello !
Here is finally the 1st article for the PS4 in relation to my work!
Today we are going to talk about the “OrbisSWU” tool which manages the PS4 update system.
Controlled PS4 update
OrbisSWU is a special application stored in all PUPs on the PS4. It allows updating the firmware of the PS4. Kernel, Application, Blueray Reader and WiFi / Bluetooth Chipset. Everything goes through him.
It all starts in the SceShellUI, when your PS4 requests to do an update, it will start by recovering it in a specific folder. Luckily. SceShellUI is an application that actually loads a C # coded .exe (yes, yes) based on Mono. This library is called app.exe.sprx.
It will suffice to recover this library from the FTP of xVortex (which has the particularity of decrypting executables from PS4 to ELF). Then extract the Windows executable.
Hexadecimal view of the PS4 library containing the executable
DoUpdateJob.cs in app.exe.sprx
The SceShellUI will copy the PUP into space /update/PS4UPDATE.PUP and extract the orbis_swu.elf. Then, a restart in update mode will be initiated.
During startup, the mini-syscore (process 1 after loading the kernel) will check in which mode it should be loaded.
The mini-syscore checks which mode it should load when starting the console, here the "update" mode.
Once the update mode is initiated, the executable orbis_swu.self previously extracted will be executed by the console by means of the sc_spawn function.
Launch of orbis_swu.self from mini-syscore using update mode
During its execution, the PUP will be fully decrypted. PUPs are update files made up of “blobs”, encrypted parts, sometimes compressed which will be decrypted one by one by the SAMU (The security processor of the PlayStation 4).
A list of blobs for Firmware 5.05, here the signature is in md5 and corresponds to the encrypted version. The content of the files is decrypted.
The blobs between them form different types of files, here is a (small) list of files that we can find inside:
1, ???, / dev / sflash0s0x32b
2, ???, / dev / sflash0s0x33
3, ???, / dev / sflash0s0x38
3, ???, wlan_firmware.bin
4, ???, / dev / sflash0s1. cryptx2b
5, secure_modules.bin, /dev/sflash0s1.cryptx3b
6, system.img, /dev/da0x4b.crypt
7, ???, / dev / da0x2
8, eap.img, /dev/da0x3.crypt
9, recovery .img, /dev/da0x0.crypt
10, /dev/sflash0s1.cryptx40
11, /dev/da0x1.crypt
11, preinst.img
12, system_ex.img, /dev/da0x5b.crypt
13, / dev / sflash0s0x32b
14, / dev / sflash0s0x33
To decrypt the PUP, the PS4 will use a command list (ioctl) for the "device" /dev/pup_update0:
| Function name | Order ID |
| Decrypt PUP Header | 0xC0184401 |
| Verify Segment (1) | 0xC0184402 |
| Verify Segment (2) | 0xC0184403 |
| Verify BLS Header | 0xC010440D |
| Decrypt Segment | 0xC0184404 |
| Decrypt Segment Block | 0xC0284405 |
It should be noted that the SAMU (Security Coprocessor) refuses to decrypt PUPs of version lower than the current version, it is one of the security mechanisms which detects attempts to downgrade.
Once the songs have been decrypted, Orbis_SWU will use specialized functions to update the different parts of the console, such as the BlueRay player, the Wifi / Bluetooth chipset, etc.
A small part of the functions of orbis_swu.self
Launching the update outside of Update Mode
It is possible to launch the update utility without putting the console in update mode, it can still update the components of the PS4. To do so, you need a Kernel exploit, the H (omebrew) EN (abler), and the make_fself.py of Flat_Z
The idea is that through a Homebrew "Hosts", to execute a modified orbis_swu.self which will do what we want. Just use the function
Code:
sceSystemServiceLoadExec(char* path, void* unk);- Modifying the video output: orbis_swu is normally used in a context where SceShellUI does not exist. It will now be necessary to indicate to him that he must take the exit of the Applications.
- Give it permissions: Like any system process, orbis_swu must be able to access certain things. It will therefore be necessary to give it special permissions and to make it escape from its sandbox through a system call. It is also necessary to patch the kernel to be able to have access to the sflash in writing.
Modification of the "start" to execute a syscall (here 67) which will simply delete the sandbox from the application.
Here, the ESI register (Argument 2) must be set to 0 to set it to MAIN
Once this is done, your homebrew is ready to use the orbis_swu to perform updates! Now is when things start to get interesting!
The orbis_swu.self launched without the presence of an update.
Case 1: Update a PS4 without Blu-ray player
The first possible use of this is to bring in the update of consoles without Blu-ray player possible.
Code:
BdWriter::checkDeviceExist -1PupReader::checkSegmentUpdate initialize failed: 0x801809a8 PupReader::Estimate::2019 checkSegmentUpdate failed: 0x801809a8 [ERROR]sceUpdaterVerifySign() failed : 801809a8
Code:
BdWriter::checkDeviceExistcannotThe location of the error display
The patch will be very simple, it will suffice to modify the instruction to return the error with a
Code:
xor ebx, ebx
Code:
mov eax, ebxThe instruction to modify
Tadaaaa! PS4 updates even without Blu-ray player
PS4 update without being in update mode
Case 2: Downgrade attempt
Even if it may seem fanciful to try to downgrade in the simplest way possible, it is still necessary that this process recalls the downgrade of the PSVita Modoru by TheFlow which runs its update module to downgrade with a modified version.
Here the idea is simple, if the PS4 cannot decrypt blobs of PUP lower than its version, we will decrypt them for him. The attack is simple, we will hook (hook) the syscall dedicated to ioctl and intercept the calls made to the "device" of decryption then:
- Make an MD5 signature of the encrypted version
- Find the decrypted version in a USB key
- Return the decrypted version without using the SAMU
"Ioctl" syscall hook is hooking useful functions.
Once this was in place, I was surprised that it worked! The PS4 has accepted the update!
However, an error at the Switch Bank level. Which cancels the update and switches back to the current version (The backup bank)
Error 0x8018085F (SCE_UPDATER_CORE_ERROR_PUP_US_NEEDAUTH)
After analysis of the SFLASH, it is possible to notice that values have all the same changed, such as the version of this one.
I continue my research to know how to correct the switch bank and why not have the possibility of Downgrade ^^
I hope that the article will have you more, I continue my work. Ciao!
Source:
- Payload Kernel based on Golden's work: https://github.com/jogolden/ps4-ksdk
- IDC ps4_pup_unpack: https://github.com/idc/ps4-pup_unpack/
- TheUpdaterToolkit: https://github.com/theorywrong/TheUpdaterToolkit/
- Zecoxao and LightningMods for their aid and their participation in research is in the development of PoC.