Not long ago news of a PS4 Root Privilege Escalation & Prison Break / Sandbox Break PoC was confirmed, and today kr105 dropped word in the Shoutbox that a usable dlclose exploit for PS4 Firmware 1.76 is now available to compile with CTurt's open-source work! 
Download: PS4-dlclose-master.zip / PS4 Dlclose GIT / GIT / Linux Loader Patch for 1.76 / bzImage / initramfs.cpio.gz by kr105 / PS4 Playground / PS4 Playground GIT / ps4link-master.zip / PS4Link GIT
From the ReadMe Files: PS4-dlclose
 Fully implemented dlclose exploit for PS4 fw 1.76. Compile it with CTurt's.
Fully implemented dlclose exploit for PS4 fw 1.76. Compile it with CTurt's.
This is the bare working exploit, you must add your own payload code to make it do anything useful. Enjoy!
Linux loader
Patches for decrypt_pup_header (1.76):
Revisiting the Original PS4 Jailbreak 1.76

Download: PS4-dlclose-master.zip / PS4 Dlclose GIT / GIT / Linux Loader Patch for 1.76 / bzImage / initramfs.cpio.gz by kr105 / PS4 Playground / PS4 Playground GIT / ps4link-master.zip / PS4Link GIT
From the ReadMe Files: PS4-dlclose
 Fully implemented dlclose exploit for PS4 fw 1.76. Compile it with CTurt's.
Fully implemented dlclose exploit for PS4 fw 1.76. Compile it with CTurt's.This is the bare working exploit, you must add your own payload code to make it do anything useful. Enjoy!
Linux loader
Code:
@@ -28,6 +28,15 @@ If you're on Linux, the easiest way is probably to use `netcat`:
After you have sent the binary, it will be executed automatically.
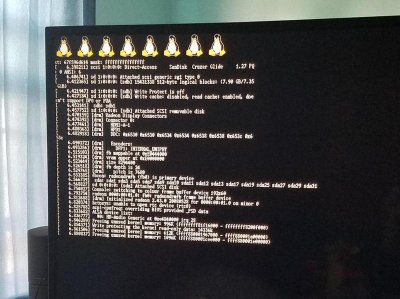
+### Linux loader
+You need a FAT32 formatted USB drive plugged in on any PS4's USB port with the following files on the root directory:
+
+`bzImage` : Kernel image that will be loaded. Recommended to use [this sources](https://github.com/fail0verflow/ps4-linux/tree/ps4-xhci-wip) to compile it.
+
+`initramfs.cpio.gz` : The initial file system that gets loaded into memory during the Linux startup process. [This one](https://github.com/slashbeast/better-initramfs) is recommended.
+
+The file names must match with the above and you can have more files on the same USB drive. From there you can setup the environment to run from an NFS share or from an external drive via USB (recommended) and boot a complete distro!
+
### Syscalls
`Get PID` - Get process ID
Code:
*(uint16_t *) 0xFFFFFFFF827C445C = 0x9090;
*(uint16_t *) 0xFFFFFFFF827C446B = 0x9090;
*(uint16_t *) 0xFFFFFFFF827C4470 = 0x9090;
