Proceeding Flat_z's Write-up, the PS4 Backporting Method Outline and his recent PKGEditor EKPFS / XTS Key Support updates, PlayStation 4 developer maxton shared on Github some handy Package information including details on PS4 PKG encryption developer-controlled keys, PFS key generation, the ENTRY_KEYS entry, the IMAGE_KEY entry, how to decrypt PKGs and PKG authentication. 
This also comes following the PFS Protection Bypass method, PFS Explorer Support for GameArchives (Latest Version) archive explorer, PS Vita PlayStation File System Keys, MakePFS, PS4 Sealedkey / pfsSKKey details for savegame and trophy data decryption, a PSFSKKey savegame decryption tool (lacking SAMU PFS keys) and the PFS Structure.
From the LibOrbisPkg Wiki via maxton on Github, to quote: PKG Information
The PS4 Dev Wiki has some information on PKGs and PFS images. Also check out flatz's write-up on Fake PKGs.
Anyway, here's some information about PKGs I've discovered in making this library and toolset.
PKG Encryption
Developer-controlled keys
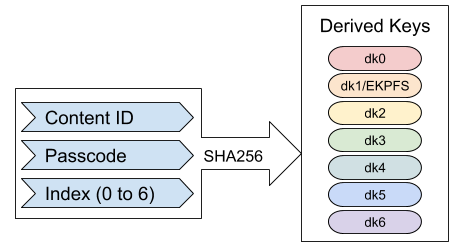
The contents of a PKG are encrypted with keys derived from a developer-specified passcode and the Content ID.
Let's call these derived keys dk0 to dk6 based on the index value used to create them.
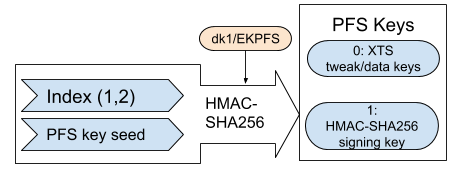
To generate keys for PFS, the PFS key seed is combined with an index and then hashed with HMAC-SHA256 using the dk1 (EKPFS) as a key. Index 1 generates XTS tweak and data keys, while index 2 generates the HMAC-SHA256 signing key.
The ENTRY_KEYS entry
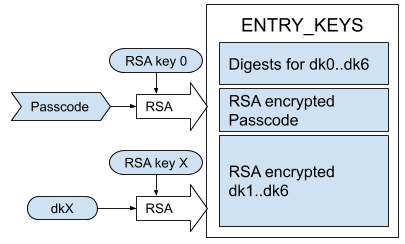
6 of the derived keys are encrypted using public-key RSA and stored in the ENTRY_KEYS entry. Their digests are also stored there. Each derived key gets encrypted with a unique RSA key. The passcode is stored in place of dk0 and it gets its own RSA key as well.
We only have public moduli for these RSA keys; except RSA Key 3, for which we have the public and private keys. This entry is stored unencrypted in the PKG, so to access the passcode, for example, all you'd need is the private RSA key 0.
The IMAGE_KEY entry
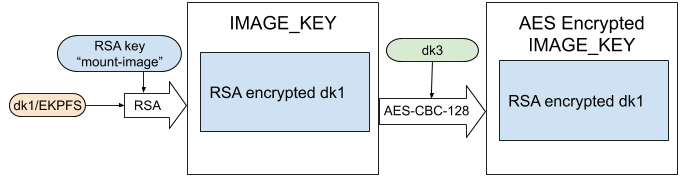
The EKPFS (dk1) is RSA encrypted with the "mount-image" public key and stored in IMAGE_KEY. We don't have the private "mount-image" RSA key, which is why for FAKE PKGs we actually replace it with flatz's generated mount-image key for Fake PKGs.
This allows us to decrypt FAKE PKGs without a passcode or license, the same way flatz illustrated in his Fake PKG kernel patches in the write-up.
Ok, whatever, but just tell me how do I decrypt some PKG I have?
So, if you want to decrypt the PFS image of any PKG, only one of the following items is required:
For Fake PKGs, we have replaced item 3 with our own key so we can already decrypt any Fake PKG using PkgEditor or PkgTool.
PKG Authentication
PKG files utilize SHA-256, HMAC-SHA256, and RSA to authenticate and prevent tampering.
Spoiler
Cheers to Figure03 for the heads-up on this over the weekend!
 Also heating things up on Twitter today from @SpecterDev, to quote:
Also heating things up on Twitter today from @SpecterDev, to quote:
After many months of work in collaboration with diwidog and CrazyVoidPS4 w/ help from flat_z, we have a hello world homebrew app running on the PS4 built with a custom toolchain / non-sony ***! Still work to be done, but this is a big step for homebrew.

This also comes following the PFS Protection Bypass method, PFS Explorer Support for GameArchives (Latest Version) archive explorer, PS Vita PlayStation File System Keys, MakePFS, PS4 Sealedkey / pfsSKKey details for savegame and trophy data decryption, a PSFSKKey savegame decryption tool (lacking SAMU PFS keys) and the PFS Structure.
From the LibOrbisPkg Wiki via maxton on Github, to quote: PKG Information
The PS4 Dev Wiki has some information on PKGs and PFS images. Also check out flatz's write-up on Fake PKGs.
Anyway, here's some information about PKGs I've discovered in making this library and toolset.
PKG Encryption
Developer-controlled keys
The contents of a PKG are encrypted with keys derived from a developer-specified passcode and the Content ID.
Let's call these derived keys dk0 to dk6 based on the index value used to create them.
- dk1 is what flatz/sony refer to as EKPFS. It is used to generate PFS encryption and signing keys.
- dk2 is used to generate the AES iv/key to encrypt the license.info in the PKG entry filesystem.
- dk3 is used to generate the AES iv/key to encrypt the IMAGE_KEY entry, the license.dat, and to encrypt the PKG header signature.
- It is not known if the other derived keys are used for anything. They can be used to encrypt entries in the PKG entry filesystem, but so far I've only seen dk2 and dk3 used for that.
To generate keys for PFS, the PFS key seed is combined with an index and then hashed with HMAC-SHA256 using the dk1 (EKPFS) as a key. Index 1 generates XTS tweak and data keys, while index 2 generates the HMAC-SHA256 signing key.
The ENTRY_KEYS entry
6 of the derived keys are encrypted using public-key RSA and stored in the ENTRY_KEYS entry. Their digests are also stored there. Each derived key gets encrypted with a unique RSA key. The passcode is stored in place of dk0 and it gets its own RSA key as well.
We only have public moduli for these RSA keys; except RSA Key 3, for which we have the public and private keys. This entry is stored unencrypted in the PKG, so to access the passcode, for example, all you'd need is the private RSA key 0.
The IMAGE_KEY entry
The EKPFS (dk1) is RSA encrypted with the "mount-image" public key and stored in IMAGE_KEY. We don't have the private "mount-image" RSA key, which is why for FAKE PKGs we actually replace it with flatz's generated mount-image key for Fake PKGs.
This allows us to decrypt FAKE PKGs without a passcode or license, the same way flatz illustrated in his Fake PKG kernel patches in the write-up.
Ok, whatever, but just tell me how do I decrypt some PKG I have?
So, if you want to decrypt the PFS image of any PKG, only one of the following items is required:
- RSA key 0 (public modulus starts d6 aa 0c 5c)
- RSA key 1 (public modulus starts b9 69 53 ee)
- The mount-image RSA key
- The passcode
- The EKPFS
- The XTS data and tweak keys
For Fake PKGs, we have replaced item 3 with our own key so we can already decrypt any Fake PKG using PkgEditor or PkgTool.
PKG Authentication
PKG files utilize SHA-256, HMAC-SHA256, and RSA to authenticate and prevent tampering.
Spoiler
Cheers to Figure03 for the heads-up on this over the weekend!
After many months of work in collaboration with diwidog and CrazyVoidPS4 w/ help from flat_z, we have a hello world homebrew app running on the PS4 built with a custom toolchain / non-sony ***! Still work to be done, but this is a big step for homebrew.

