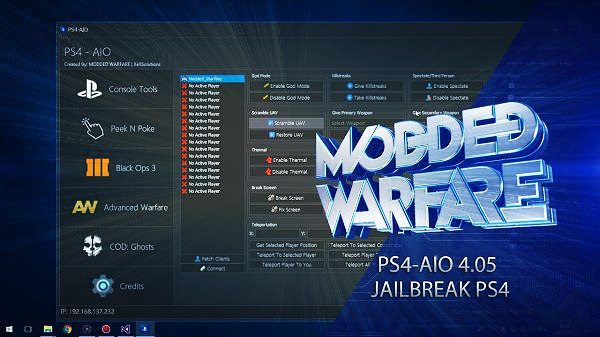
Following his previous update, today PlayStation 4 developer @MODDEDWARFARE made available PS4 AIO v1.4.0 with a new demo video on his YouTube Channel which includes exploited 4.05 Firmware support alongside BO3 mods followed by v1.5.0! 
Download: PS4-AIO-Setup 1.4.0.exe (42.6 MB) / PS4 AIO Portable 1.4.0.zip (42.1 MB) / PS4 AIO v1.5.0
To quote from the video's caption: PS4-AIO Release with 4.05 Support & BO3 Mods! (PS4 Jailbreak)
Here's an updated version of my PS4-AIO tool which now supports 4.05.
Please download and install the latest version rather than trying to update any older versions.
Playing Ghosts For Free & Cool Mods On 4.05 (PS4 Jailbreak & Homebrew)
[PS4/BO3] Real Time Editing using my own tool (God Mode, Ammo, Points, etc..)
[PS4/RELEASE] Open Source Black Ops III Zombie RTM Tool [5.05/4.55/4.05]
Download: PS4 RTM Tool MrNiato v1.0.zip / PS4 RTM Tool MrNiato v1.0.zip (Mirror) / PS4 RTM Tool MrNiato v1.0.zip (1.26.zip) via MrNiato, to quote: HOW TO:
1) With your PS4 go to this link: http://crack.bargains/505k/
2) If you have message "Youre all set!" close the browser and reopen it again then you will have a message "Awaiting Payload...".
3) Open NETCAT GUI, change your IP Adress with the one of your PS4, change "9023" by "9020", select the payload in the folder then inject it !
4) Launch Black ops III in Zombie mod, connect the PS4 and.... enjoy !!
Download: PS4-AIO-Setup 1.4.0.exe (42.6 MB) / PS4 AIO Portable 1.4.0.zip (42.1 MB) / PS4 AIO v1.5.0
To quote from the video's caption: PS4-AIO Release with 4.05 Support & BO3 Mods! (PS4 Jailbreak)
Here's an updated version of my PS4-AIO tool which now supports 4.05.
Please download and install the latest version rather than trying to update any older versions.
Playing Ghosts For Free & Cool Mods On 4.05 (PS4 Jailbreak & Homebrew)
[PS4/BO3] Real Time Editing using my own tool (God Mode, Ammo, Points, etc..)
[PS4/RELEASE] Open Source Black Ops III Zombie RTM Tool [5.05/4.55/4.05]
Download: PS4 RTM Tool MrNiato v1.0.zip / PS4 RTM Tool MrNiato v1.0.zip (Mirror) / PS4 RTM Tool MrNiato v1.0.zip (1.26.zip) via MrNiato, to quote: HOW TO:
1) With your PS4 go to this link: http://crack.bargains/505k/
2) If you have message "Youre all set!" close the browser and reopen it again then you will have a message "Awaiting Payload...".
3) Open NETCAT GUI, change your IP Adress with the one of your PS4, change "9023" by "9020", select the payload in the folder then inject it !
4) Launch Black ops III in Zombie mod, connect the PS4 and.... enjoy !!


