I have been messing around with trying to get my VR headset to work with 4.05 for a little while, and because the VR headset is updated to the latest firmware it wouldn't work.
Just recently @XVortex pointed out you can poke a memory value to sort of spoof the system firmware version, so I tried what he said and put together a Enable_VR.bin payload (load the HEN payload and then load the VR payload because the Web exploit will say invalid import map, or use this idc.zip modified IDC exploit to launch it as I have added the 5.05 sections so it does not complain about import map) to poke the offset and found it allowed my VR headset to work.
 Update: Ok I sorted out the problem and merged the enable VR mod into XVortex's HEN 1.3 so you can now just run this 1 HEN payload and play VR with the source code below:
Update: Ok I sorted out the problem and merged the enable VR mod into XVortex's HEN 1.3 so you can now just run this 1 HEN payload and play VR with the source code below:
Download: ps4-hen-VR.zip (0.01 MB) / ps4-hen-VR.tar.gz (0.05 MB - Source Code) / usb_hen_vr.zip (0.03 MB - for USB Stick) / Ps4_Serve_v1_8.apk / Enable_VR_455.zip / usb_455_vr_enable.zip (0.02 MB) / ps4-hen-VR.zip (0.01 MB) / Enable-VR-50X
I only have 1 VR game to test on at the moment as I have to download the VR games now, but it is Resident Evil 7 and its working with my latest updated VR 3.10 and 4.05 + HEN.
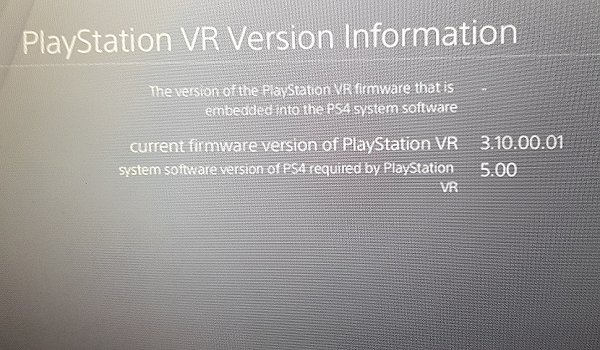
Huge thanks to @XVortex, as you can see this is my VR information:
And this is the game running on VR:

Tested a few more VR games and all works well:
Rush of Blood:

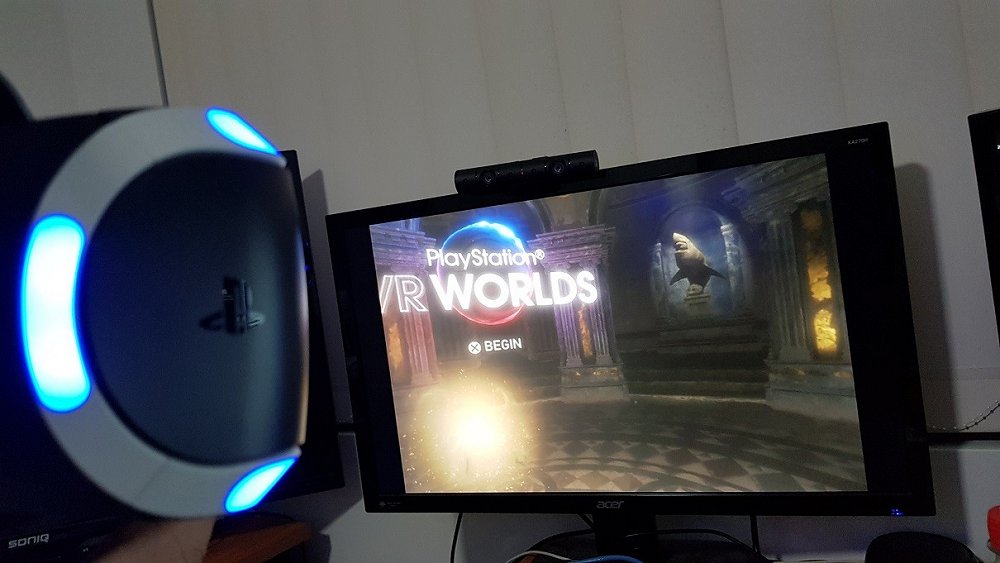
VR Worlds:
Arkham VR:

Just recently @XVortex pointed out you can poke a memory value to sort of spoof the system firmware version, so I tried what he said and put together a Enable_VR.bin payload (load the HEN payload and then load the VR payload because the Web exploit will say invalid import map, or use this idc.zip modified IDC exploit to launch it as I have added the 5.05 sections so it does not complain about import map) to poke the offset and found it allowed my VR headset to work.
Download: ps4-hen-VR.zip (0.01 MB) / ps4-hen-VR.tar.gz (0.05 MB - Source Code) / usb_hen_vr.zip (0.03 MB - for USB Stick) / Ps4_Serve_v1_8.apk / Enable_VR_455.zip / usb_455_vr_enable.zip (0.02 MB) / ps4-hen-VR.zip (0.01 MB) / Enable-VR-50X
I only have 1 VR game to test on at the moment as I have to download the VR games now, but it is Resident Evil 7 and its working with my latest updated VR 3.10 and 4.05 + HEN.
Huge thanks to @XVortex, as you can see this is my VR information:
And this is the game running on VR:
Tested a few more VR games and all works well:
Rush of Blood:
VR Worlds:
Arkham VR:

