Another Festivus miracle... proceeding the PS4 9.00 Payloads, Caturday arrived early for the PS4Scene as ChendoChap (BTC: bc1qswmgpt7akstzrsudefjj88e7caxgmqfaxt59rf) just released the PS4 9.00 Jailbreak Exploit dubbed POOBS4 following @sleirsgoevy's PS4 9.00 Webkit Exploit for use in PlayStation 4 Jailbreaking consoles up to PS4 9.00 OFW as @SpecterDev confirmed it was patched in 9.03 PS4 OFW... to reiterate, this means if you update your PlayStation 4 console software above 9.00 you will NOT be able to jailbreak it at this time! 

Also released in conjunction with today's pOOBs4 PS4 9.00 Kernel Exploit and PS4 Payloads for 9.00 Firmware are a Mira ELF / Loader for enabling homebrew (ELF: port 9021, Loader: port 9020) via SpecterDev and a GoldHEN 9.00 PS4 Payload via _AlAzif to run the latest PS4 PKG Games (Part II).

Download: pOOBs4-main.zip (22.6 KB - includes exfathax.img) / GIT / 9.00 Host Live Demo / 9.00 Host GIT / Mira 9.00.zip (116 KB - includes Mira_Orbis_MIRA_PLATFORM_ORBIS_BSD_900.elf and MiraLoader_Orbis_MIRA_PLATFORM_ORBIS_BSD_900.bin) / payloads (3.50.9.00).zip (223.66 KB) / goldhen_2.0b_900.bin (224 KB - Fixed) / ps4-dumper-vtx-900.bin / Al Azif's DNS Exploit Menu IPs / PS4JB pOOBs4 for 9.00 with GoldHEN Autoload / 9.00_kernel.bin (20.08 MB) / USBHack.zip (6.23 KB - includes USBHack.img - a better? image file for USB drives to replace exfathax.img) per mrdude, to quote:
Here you go people, I have created a better image file for your usb drives to replace exfathax.img. This is better for the following reasons:
With exfathax.img there is an error dispalyed on the ps4 because the exfat file system doesn't exist and the ps4 can see that there is an error in the usb file system. I have created a new image which fixes this error and has a very tiny exfat partition only a few bytes, but stil shows up on pc without the need to format error. This also stops the usb error message showing up on the ps4. This should make booting into the hack easier.
To use - just use win32diskimager to write to the image to your usb drive. You can also create a partition on the existing space on your usb drive and use that on the ps4 for installing pkg files.
I tried to post this on poobs4 github but there's no way to post on that page, so I'll release here and someone can pass it on.
Spoiler: Depreciated
 Those interested in exploiting their 9.00 or below PlayStation 4 console can either use @Al Azif's DNS IPs above or host it yourself following the previous guides linked below, keeping in mind our stance on clone hosts remains the same on the forums here... spam them and get banned.
Those interested in exploiting their 9.00 or below PlayStation 4 console can either use @Al Azif's DNS IPs above or host it yourself following the previous guides linked below, keeping in mind our stance on clone hosts remains the same on the forums here... spam them and get banned.
 Below is pOOBs4's README.md... this requires a specially formatted USB device (ExFAT Bug also affects PS5
Below is pOOBs4's README.md... this requires a specially formatted USB device (ExFAT Bug also affects PS5  ) so read it VERY CAREFULLY to ensure developers including Al Azif aren't inundated with questions already covered... @RF0oDxM0Dz reports stability is similar to 5.05 and "better than 6.72 and 7.xx" with @Al Azif stating the success rate from feedback is "already is a world of difference from 6.72, 7.02, and 7.5X" so without further ado:
) so read it VERY CAREFULLY to ensure developers including Al Azif aren't inundated with questions already covered... @RF0oDxM0Dz reports stability is similar to 5.05 and "better than 6.72 and 7.xx" with @Al Azif stating the success rate from feedback is "already is a world of difference from 6.72, 7.02, and 7.5X" so without further ado:
PS4 9.00 Kernel Exploit
Summary
In this project you will find an implementation that tries to make use of a filesystem bug for the PlayStation 4 on firmware 9.00. The bug was found while diffing the 9.00 and 9.03 kernels. It will require a drive with a modified exfat filesystem. Successfully triggering it will allow you to run arbitrary code as kernel, to allow jailbreaking and kernel-level modifications to the system. will launch the usual payload launcher (on port 9020).
Patches Included
The following patches are applied to the kernel:
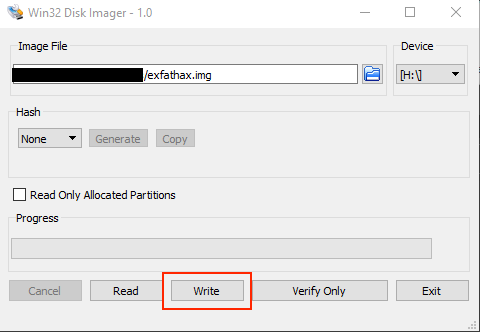
This exploit is unlike previous ones where they were based purely in software. Triggering the vulnerability requires plugging in a specially formatted USB device at just the right time. In the repository you'll find a .img file. You can write this .img to a USB using something like Win32DiskImager.
Note: This will wipe the USB drive, ensure you select the correct drive and that you're OK with that before doing this
When running the exploit on the PS4, wait until it reaches an alert with "Insert USB now. do not close the dialog until notification pops, remove usb after closing it.". As the dialog states, insert the USB, and wait until the "disk format not supported" notification appears, then close out of the alert with "OK".
It may take a minute for the exploit to run, and the spinning animation on the page might freeze - this is fine, let it continue until an error shows or it succeeds and displays "Awaiting payload".
Notes
Special Thanks
 Twitter Tweets
Twitter Tweets
Spoiler: PS4 Alternative USB Flash Drive Method by SMD
 Finally, if you haven't done so yet check out both the Downloading PS4 PKG Games That Are Base64 Encoded or Torrents Guide and PS4 Fake PKG (FPKG) Sharing Guide to become Verified via the 'floating' Discord Channel and get your Blue Verified Badge for the latest PS4 Game PKGs!
Finally, if you haven't done so yet check out both the Downloading PS4 PKG Games That Are Base64 Encoded or Torrents Guide and PS4 Fake PKG (FPKG) Sharing Guide to become Verified via the 'floating' Discord Channel and get your Blue Verified Badge for the latest PS4 Game PKGs! 

Also released in conjunction with today's pOOBs4 PS4 9.00 Kernel Exploit and PS4 Payloads for 9.00 Firmware are a Mira ELF / Loader for enabling homebrew (ELF: port 9021, Loader: port 9020) via SpecterDev and a GoldHEN 9.00 PS4 Payload via _AlAzif to run the latest PS4 PKG Games (Part II).
Download: pOOBs4-main.zip (22.6 KB - includes exfathax.img) / GIT / 9.00 Host Live Demo / 9.00 Host GIT / Mira 9.00.zip (116 KB - includes Mira_Orbis_MIRA_PLATFORM_ORBIS_BSD_900.elf and MiraLoader_Orbis_MIRA_PLATFORM_ORBIS_BSD_900.bin) / payloads (3.50.9.00).zip (223.66 KB) / goldhen_2.0b_900.bin (224 KB - Fixed) / ps4-dumper-vtx-900.bin / Al Azif's DNS Exploit Menu IPs / PS4JB pOOBs4 for 9.00 with GoldHEN Autoload / 9.00_kernel.bin (20.08 MB) / USBHack.zip (6.23 KB - includes USBHack.img - a better? image file for USB drives to replace exfathax.img) per mrdude, to quote:
Here you go people, I have created a better image file for your usb drives to replace exfathax.img. This is better for the following reasons:
With exfathax.img there is an error dispalyed on the ps4 because the exfat file system doesn't exist and the ps4 can see that there is an error in the usb file system. I have created a new image which fixes this error and has a very tiny exfat partition only a few bytes, but stil shows up on pc without the need to format error. This also stops the usb error message showing up on the ps4. This should make booting into the hack easier.
To use - just use win32diskimager to write to the image to your usb drive. You can also create a partition on the existing space on your usb drive and use that on the ps4 for installing pkg files.
I tried to post this on poobs4 github but there's no way to post on that page, so I'll release here and someone can pass it on.
Spoiler: Depreciated
- PS4 Official Firmware (OFW) Archives
- PS4 Game Firmware Lists
- PS4 Exploit Hosting Tutorial
- PS4 Exploit Hosting Video Guides
- Android PS4 Exploit Host
- xPloitServer Host
- PlayStation 4 Tool Box 2.1.10.286
- PS4 ELF Injectors & Payload Loaders / PS4 Payload Sender
- PS4 Payload Sender in React Native for Android (APK)
PS4 9.00 Kernel Exploit
Summary
In this project you will find an implementation that tries to make use of a filesystem bug for the PlayStation 4 on firmware 9.00. The bug was found while diffing the 9.00 and 9.03 kernels. It will require a drive with a modified exfat filesystem. Successfully triggering it will allow you to run arbitrary code as kernel, to allow jailbreaking and kernel-level modifications to the system. will launch the usual payload launcher (on port 9020).
Patches Included
The following patches are applied to the kernel:
- Allow RWX (read-write-execute) memory mapping (mmap / mprotect)
- Syscall instruction allowed anywhere
- Dynamic Resolving (sys_dynlib_dlsym) allowed from any process
- Custom system call #11 (kexec()) to execute arbitrary code in kernel mode
- Allow unprivileged users to call setuid(0) successfully. Works as a status check, doubles as a privilege escalation.
- (sys_dynlib_load_prx) patch
- Disable delayed panics from sysVeri
This exploit is unlike previous ones where they were based purely in software. Triggering the vulnerability requires plugging in a specially formatted USB device at just the right time. In the repository you'll find a .img file. You can write this .img to a USB using something like Win32DiskImager.
Note: This will wipe the USB drive, ensure you select the correct drive and that you're OK with that before doing this
It may take a minute for the exploit to run, and the spinning animation on the page might freeze - this is fine, let it continue until an error shows or it succeeds and displays "Awaiting payload".
Notes
- You need to insert the USB when the alert pops up, then let it sit there for a bit until the ps4 storage notifications shows up.
- Unplug the USB before a (re)boot cycle or you'll risk corrupting the kernel heap at boot.
- The browser might tempt you into closing the page prematurely, don't.
- The loading circle might freeze while the webkit exploit is triggering, this means nothing.
- This bug works on certain PS5 firmwares, however there's no known strategy for exploiting it at the moment. Using this bug against the PS5 blind wouldn't be advised.
Special Thanks
Spoiler: PS4 Alternative USB Flash Drive Method by SMD

